- T-#
- A set of AT&T physical channel standards for the DS-# digital carrier standards. It’s common (but sloppy) practice to refer to DS-# signals as T-#. A T-1 line has 100Ω characteristic impedance. There is no T-0. See DUV.
- T568
- Refers to the EIA/TIA wiring standards T568A and T568B for Cat# network cables.
- tablet
- A mobile computer smaller than the older netbook, with a touchscreen interface, solid-state storage, and support for one or more types of wireless connectivity: PANs (e.g. Bluetooth), wireless LANs (e.g. 802.11), and sometimes even mobile phone systems (3G or later). Apple’s iPad is the best-known.
- TACAN
- Tactical Air Navigation. A UHF air navigation aid, still (2010) in operation but, like its cousin LORAN, being supplanted by GPS. Aircraft with TACAN receivers can determine distance and bearing to TACAN stations up to 300 miles away. U.S. stations have 126 receive channels at 1025-1150 MHz and 126 transmit channels at 962-1024 or 1151-1213 MHz.
- TACS
- Total Access Communications System. An analog cellular telephone system deployed mainly in Europe, and now obsolete. It used FM and FDMA. There were two types. ETACS offered 1240 channels with 25 kHz channel spacing. Its receiving channels occupied the 916-949 MHz spectrum, and its transmitting channels were at 871-904 MHz. NTACS offered 400 channels with 12.5 kHz channel spacing. Its receiving channels occupied the 860-870 MHz spectrum, and its transmitting channels were at 915-925 MHz.
- tandem switch
- A telephone switch that connects one trunk line to another.
- tank circuit
- Also called a parallel resonant circuit or a LC circuit, because it consists of a capacitance C and inductance L in parallel. Inductive current lags and capacitive current leads a changing voltage by 90°, so their AC currents always have opposite phase. At some resonant frequency f = 1 / [2π (LC)½], the opposite currents are equal and no net current flows. The tank circuit is therefore a BPF or BSF, depending on where it’s placed, with bandwidth proportional to C and inversely proportional to L.
- This ideal model ignores the resistance that accompanies real-world C and L. See RLC.
- TAO
- Tailored Access Operations. (2013) A group within the National Security Agency that finds exploits for hacking computer systems.
- TAPI
- Telephony Applications Programming Interface. See API.
- tap points
- The stages in a shift register (buffer) that are tapped to produce a linear recursive sequence, which is used in channel coding, pseudo-random noise generation, cyclic redundancy checks (CRC), etc. The tap points are usually given in the form of a generating polynomial (GP), e.g. [x23 + x18 + 1]. See LFSR.
- tar
- From “tape archive”. A Unix command for backing up data to a magnetic tape drive. The resulting file, known as a tarball, has the .tar filename extension. Members of the GNU/Linux community still use
tarto create file bundles for sharing or archiving (not so much on magnetic tape), but commonly use a separate compression tool as well. For example, tarballs compressed with the gzip or 7zip utilities typically have the filename extension .tar.gz or .tgz. MS Windows 10 has the native ability to unpack these files, but earlier versions of Windows don’t. - TBU
- Transient Blocking Unit. A circuit component that protects the rest of the circuit from short-lived current spikes (transients). It can use either or both of two approaches: current-limiting to block the spike, and shunting excess current to ground. The former provides a faster response, but the latter, known as a TVS, can handle higher power levels.
- TCAM
- Ternary Content Addressable Memory. See CAM.
- TCK
- Test Clock. The JTAG bus clock signal line.
- TCM
- Trellis Coded Modulation. A combined coding and QAM technique to improve signal quality without increasing required bandwidth or signaling rate, or reducing data rate. Every k data bits are transformed into a (k+1)-bit codeword, resulting in a [2k+1]-point signal constellation. The symbols (points of the constellation) are divided into subsets such that the symbols of each subset are at a maximum free Euclidean distance from one another, making them easier to distinguish. (See Gray coding.)
- The rules of a trellis code stipulate sequences in which these subsets may be used. The use of one subset restricts the possible choices for the next symbol to half of the other subsets. Given this predictability, the signal is decoded using soft-decision, maximum-likelihood decoding (the Viterbi algorithm) to minimize error. As determined by Gottfried Ungerboeck, doubling the number of symbols (from 2k to 2k+1) yields almost all of the achievable coding gain, usually 3 to 6 dB. Going to 2k+2, etc., isn’t worth it, so rate k/[k+1] trellis codes are the rule.
- TCO
- (1)
- Tjänstemännens Centralorganisation (Swedish for “Confederation of Professional Employees”). A Swedish standard for readily recycled, low-power, low-emission monitors (and, since 1995, entire computers). Stricter than MPR II.
- (2)
- Total Cost of Ownership.
- t-coil
- Telecoil. A system for transmitting audio signals to hearing aids. It uses short-range magnetic induction rather than RF, and hearing aids pick up these signals on copper wire coils.
- TCP
- Transfer Control Protocol. It began as Transmission Control Program in 1973. The protocol that serves as the top layer of the TCP/IP stack. It operates at level 4 (Transport layer) of the OSI network model. Applications use it to open a packet-oriented, logical (i.e., not physical) connection to some other host over a network, and to control traffic on that link. To open the connection, the client protocol sends a SYN (synchronization) packet, the server protocol responds with a SYN-ACK, and the client then sends an ACK (acknowledgment) packet – a process called a three-way handshake. After that, the client can submit requests for the actual data it seeks.
- On wireless networks that suffer packet loss, which is most of them, a new (2012) approach called coded TCP or TCP/NC (NC = network coding) can greatly boost throughput by eliminating the need for packet retransmission. Each packet is linearly combined with other, previously sent packets selected using a set of coefficients that are in the header of every packet. If a packet is lost, the receiver can recreate it from other received packets plus the coefficents.
- TCP/IP
- Transfer Control Protocol/Internet Protocol. Also called the Internet Protocol Suite. A set of protocols, i.e. rules for communication, that provide access to packet-switched networks such as FDDI, Ethernet, and the Internet itself.
- There are hundreds of protocols to handle all the different tasks required of a network, but TCP and IP are the keystones. TCP creates connections between nodes on a network for use by applications, and manages packetization of data for the connections; IP handles the routing of each connection’s data packets. The protocol suite, or stack, divides into four layers, with each layer providing services to the layer above and/or using the services of the layer beneath:
- Application (User) – Includes BGP, BIND, Bootp, DHCP, DNS, FTP, Gopher, HTTP, IMAP, IRC, LDAP, NFS, NNTP, POP, RIP, SMTP, SNMP, SSH, Telnet, and TFTP
- Transport (Host-to-Host Communications) – Includes TCP and UDP
- Internet – Includes ICMP, IGMP, IP, IPsec, and maybe ARP
- Link (Network Access) – Includes NDP, PPP, SLIP, and maybe ARP
- The TCP/IP Application layer is equivalent to the Application, Presentation, and Session layers of the newer OSI model, and its Link layer is equivalent to OSI’s Data Link and Physical layers – sort of. TCP/IP was not designed for OSI’s layered approach, so the comparison is flawed.
- Each service associates itself with a virtual port, a 16-bit number that TCP/IP uses to organize and track its processes. The transport-level protocols, TCP and UDP, assign these ports. Many ports are unregulated, but the IANA specifies the services that must be assigned to ports 0-1023. For example, Web browsing (HTTP) uses port 80, encrypted browsing with TLS or SSL uses port 443, FTP uses ports 20 and 21, and remote access (e.g. Telnet) uses port 23. Packets sent by or to a service contain the port number.
- When an application protocol directs TCP to send a transmission over the network, TCP breaks the transmission into data packets, and appends a header to each packet with a packet number (for reassembling the transmission) and a checksum (for error checking). The source computer adds its own header as well – an Ethernet header, for example. The packets are then passed down through the protocol stack. IP has the task of getting the packets to their destination. It adds an IP header to each packet, containing the source and destination IP addresses and another checksum. At the other end, the protocol stack in the receiving computer strips off the headers in reverse order to reassemble the transmission. See socket.
- TCVCXO
- Temperature-Compensated Voltage-Controlled Crystal Oscillator. See XO.
- TCXO
- Temperature-Compensated Crystal Oscillator. An oscillator (see XO) designed to keep its output frequency stable despite temperature changes. It typically employs a network of thermistors to generate a temperature-dependent correction voltage, and applies that voltage to a varactor diode in the crystal circuit.
- TDCS
- Transform-Domain Communications System. A multiple-access modulation technology that estimates current interference and generates a waveform that notches out the interference bands.
- TDD
- (1)
- Time Division Duplexing. Time-sharing of the same bandwidth by the uplink and downlink channels in a Wideband CDMA system.
- (2)
- Test-Driven Development. A software design practice: set a test goal, write code to minimally meet it, then bring the code up to standard.
- TDFN
- Thin Dual Flat Non-leaded. See JEDEC.
- TDI
- Test Data In. The JTAG bus signal line that receives serial data.
- TDM
- Time Division Multiplexing. Placing multiple signals on a single carrier by transmitting them in short bursts timed not to coincide, usually through a high-frequency cycling switch called a commutator.
- TDMA
- Time Division Multiple Access. A type of TDM in which each connection is assigned its own time slot in a repeating time frame. Older cellular voice systems typically mux three conversations together. The term is also used to refer to US cellular phone systems that rely on this technology, particularly IS-136.
- TDO
- Test Data Out. The JTAG bus signal line that sends serial data.
- TDP
- Thermal Design Power. The maximum power (in watts) that a circuit is expected to draw while in operation, hence, the thermal load that its cooling system must be able to dissipate.
- Rising TDP is what drove the CPU market’s mid-2000s shift from ever-increasing clock speeds to multi-core architectures. Intel has begun using another metric, scenario design power (SDP), for processor chips meant for mobile applications. These processors adhere to the SDP limit in environments with less capable cooling. Intel has also staked out two new metrics called PL1 and PL2 meaning, respectively, the maximum sustained power level a processor can draw, and the maximum it can draw for short bursts. Tau is their term for the maximum duration of that short burst.
- Abnormal circumstances have always been able to cause a circuit to slightly exceed its rated TDP. A potentially more serious problem is that CPU manufacturers, particularly Intel, have been known to rely on power calculation algorithms that dramatically understate TDP. Always cross-check the number against the real-world power draw measured by independent testing organizations.
- TDR
- Time Domain Reflectometer. An instrument that uses signal reflections to measure dynamic impedance on a line, meaning that it can record the surge impedance or characteristic impedance Z0.
- TD-SCDMA
- Time Division and Synchronous Code Division Multiple Access. China’s mobile phone modulation technology, blessed by the ITU as a 3G standard. It’s a combination of TDD and synchronous CDMA, and uses QPSK or 8-PSK modulation, 1.6 MHz carrier bandwidth, and 1.28 Mc/s chip rate for a maximum 2 MB/s data rate.
- TEC
- (1)
- Thermo-Electric Cooler. A solid-state device that uses power to create a thermal gradient, drawing heat away from one surface and passing it to the other. It’s the reciprocal of the TEG.
- (2)
- Thermal Energy Conversion. Using a thermal differential to generate electricity.
- technical debt
- A software engineering term for future work that a system will require to correct problems created by past development choices. These past choices are not necessarily mistakes; sometimes developers knowingly accept technical debt to meet a short-term goal.
- TED
- Technology, Entertainment, and Design. A non-profit organization (www.ted.com) dedicated to sharing transformational ideas, including but not restricted to technologies. They hold a couple of annual conferences, award prizes, etc. They’re best known for short guest speaker presentations, called TED talks, on a wide variety of topics.
- TEE
- Trusted Execution Environment. An area of computer memory and processing that’s segregated from the rest to prevent reading or tampering by outside sources.
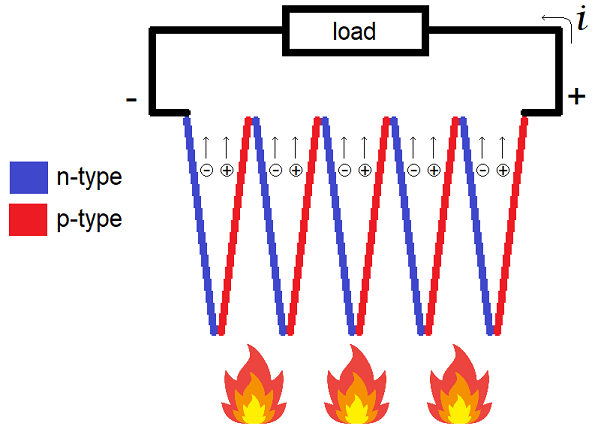
- TEG
- Thermo-Electric Generator. A solid-state energy-harvesting device that produces electric current from a heat differential using the Seebeck effect: charge carriers in a conducting or semiconducting material migrate to the cooler side. Alternating p-type and n-type semiconductors connected at each end create reinforcing voltages. Power output depends in part on the magnitude of the heat differential and the available surface area, and efficiencies are low, typically 5-10%.
- telco
- Telephone Company.
- Telcordia
- See Bellcore.
- Teledesic
- Unsuccessful 1990s LEO-based, global-coverage, Internet-via-satellite scheme backed by Bill Gates, Craig McCaw, et al.
- telegraph
- Samuel Morse invented the telegraph in 1837, and demonstrated the first practical system in 1844. It used a single wire with earth return (SWER). The inherent capacitance of long lines caused attenuation and dispersion of signals. William Thompson, Lord Kelvin modeled line behavior and established techniques for optimizing the dimensions of the conductor and insulator, and shaping the pulses. See also Morse code.
- telephone
- Bell’s original telephone used a telegraph wire, i.e. a single, uninsulated wire with earth return, and power supplied by a lead-acid battery at each phone. He later found that a balanced-line signal on a twisted pair greatly improved resistance to noise, including crosstalk that would otherwise occur when wire pairs were bundled into cables. Modern copper UTP phone cable for one or two lines has four conductors, color-coded green, red, black, and yellow (or white). The two wires of each pair are referred to as the tip (ground) and ring (either -48V or +6 to +12V). If only one line is wired, as in a standard USOC RJ11 jack, it will be the green tip 1 (pin 4 of 6) and the red ring 1 (pin 3 of 6). If there’s a second line, it uses the black tip 2 (pin 2) and yellow ring 2 (pin 5).
- telescope
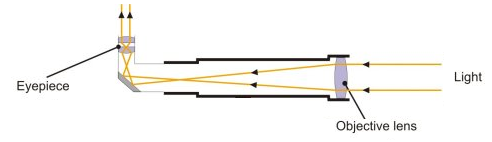
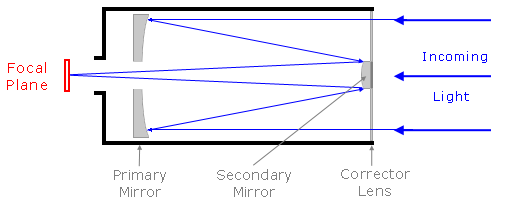
- There are three basic types of visible-light telescopes: refractors, Newtonian reflectors, and catadioptrics. Refractors are the oldest and simplest type. They use a refracting primary lens at the aperture to focus incoming light on a mirror aligned at a 45° angle at the back of the tube, reflecting the light to the eyepiece. (Older versions instead used a secondary lens to pass the light straight out the back.) Newtonian reflectors use a concave parabolic primary mirror to reflect and focus light onto a flat secondary mirror mounted at a 45° angle in the center of the tube. The secondary reflects the focused light out the side of the telescope to the eyepiece. Catadioptrics (also called “folded Cassegrains”) are the newest and most popular types. They use a concave, spherical primary mirror to reflect and focus light onto a small, convex, hyperbolic secondary mirror in the center of the aperture. The secondary, in turn, reflects the light to an eyepiece through a hole in the center of the primary.
- The two most popular catadioptric designs are Cassegrain hybrids: the Schmidt-Cassegrain (SCT) and the Maksutov-Cassegrain (MCT). The SCT uses a thin lens across the aperture to compensate for spherical aberration. The MCT employs a thicker curved lens that does the same job but is easier to make. Then there’s the Gregory-Maksutov, which replaces the MCT’s secondary mirror with a reflective spot in the center of the aperture lens.
- The names come from 17th century French sculptor Sieur Cassegrain, 20th century Estonian and Russian astronomers Bernhard Schmidt and Dmitry Maksutov, and American optical engineer John Gregory.
- Telnet
- From “Telecommunications Network”. A member of the TCP/IP protocol suite at the Application layer, this client/server protocol protocol dating from 1969 allows a user to access a command-line interface on a remote computer, via a phone line or other network. This made it an essential tool of the old BBS. Telnet also means the text-interface application that uses this protocol. The network version uses TCP port 23. Modern systems prefer SSH to Telnet.
- TEM
- (1)
- Transverse Electromagnetic. See EM.
- (2)
- Transmission Electron Microscope.
- temperature
- To convert degrees centigrade or Celsius to degrees Fahrenheit: °F = [(1.8 × °C) + 32]. Conversely, °C = [(°F - 32) / 1.8]. The Kelvin (not degrees Kelvin) scale begins at absolute zero and scales as Celsius, so absolute zero = 0 K = -273.15° C = -459.67° F. This metric conversions page includes tools for converting temperature values from all three scales.
- Air temperature, aka dry-bulb temperature, is the traditional measurement, but it gives an incomplete picture of dangers to human health. Other types:
- heat index – A temperature value that attempts to define how conditions will feel to a human, using an algorithm that factors in relative humidity as well as air temperature. There are too many variables for it to be a precise gauge of risk. As of 2023, the highest heat index ever recorded was 81° C (178° F), far beyond where NOAA’s “extreme danger” rating kicks in.
- wet-bulb temperature – A standard thermometer with a strip of wet cloth wrapped around the bulb yields a direct measurement that accounts for humidity. Prolonged exposure to wet-bulb temperatures above about 35° C (95° F) is inevitably fatal to humans. Wet-bulb temperatures below this limit can still be dangerous, depending on a number of factors.
- wind chill – The cold-temperature equivalent of heat index, wind chill uses a formula that incorporates wind speed to determine how conditions feel to a human. It works only for air temperatures below 10° C (50° F), and, like heat index, depends on some assumptions.
- TENS
- Transcutaneous Electrical Nerve Stimulation. A medical device used to treat chronic pain by applying small electric currents to the nerves of the affected area.
- tesla
- Named for pioneering engineer Nikola Tesla (1856-1943). The SI unit of magnetic flux density, one weber per square meter.
- Tesla coil
- Named for its inventor, Serbian-born engineer Nikola Tesla (1856-1943). An oscillating circuit that uses AC power and transformers to produce very high-voltage air discharges. More poetically, it’s a lightning machine. There are several design approaches; the simplified circuit below is just one.
- A high-voltage step-up transformer T1 uses an AC source to charge a large, very robust capacitor C1, which spontaneously discharges across an air-gap electrode. This causes a current inrush at the other terminal of the capacitor, which is in series with another inductor coil. This second inductor is the primary for another, loosely coupled, air-gap transformer T2. Its secondary coil takes the form of a tower topped with a toroidal terminal. If the AC source, the inductances, the capacitance, and the spark gap dimensions are chosen correctly, this design forms two mutually reinforcing tank circuits, producing a rapid, continual series of plasma streamers and long electrical arcs from the terminal of the tower coil. Compare Van de Graaff generator.
- TETRA
- Terrestrial (or Trans-European) Trunked Radio. An open digital trunked radio standard defined by ETSI.
- TeX
- From the Greek τεχ meaning skill or art, and pronounced “tek”. A computer typesetting system, i.e., a markup language for consistent, platform-independent layout of digital documents, including mathematical formulas. The output .tex files are ASCII; TeX converts them into device-independent (.dvi) files, which a DVI viewer can display or print with the correct layout. Other tools exist to convert .dvi or .tex files to, for example, PostScript or PDF format.
- Because TeX is difficult to use, there are macro packages such as LaTeX and ConTeXt that can act as intermediaries, abstracting and simplifying use of TeX instructions.
- TFEL
- Thin-Film Electro-Luminescent. A type of video display.
- TFET
- Tunneling Field Effect Transistor. See transistor.
- TFT
- Thin-Film Transistor. A field-effect transistor built by depositing thin films of doped semiconductor on an insulating substrate, as opposed to doping a semiconducting substrate. A grid of TFTs forms the active matrix in an AMLCD. Each TFT acts as an on-off switch for one to four pixels.
- Most are amorphous silicon as of 2011, but it can’t support fast enough switching speeds for new designs. Crystalline silicon, the standard for semiconductors, is too rigid, too vulnerable to cracking and moisture. Potential new TFT materials include polycrystalline silicon (poly-Si), graphene, and amorphous oxide semiconductors – oxides of metal alloys (mostly zinc, indium, gallium, and tin) that function as semiconductors when deposited in thin layers.
- TFTP
- Trivial File Transfer Protocol. A simpler 1980 version of FTP.
- TFX12V
- Thin Form-factor Extended 12-Volt. Intel 2002 specification for a PSU to support small PCs based on micro-ATX, FlexATX, and mini-ITX motherboards. A TFX PSU measures 85 mm high × 65.2 mm wide × 150 mm deep, with an 80 mm intake fan on one side.
- TGF
- Terrestrial Gamma-ray Flash. See lightning.
- T/H
- Track and Hold. A step in A/D conversion that alternates between tracking (output amplitude = input amplitude) and holding (output amplitude = input amplitude at the moment of the switch from tracking to holding) analog signal levels. Subsequent circuitry converts the hold levels to digital values. Compare S/H.
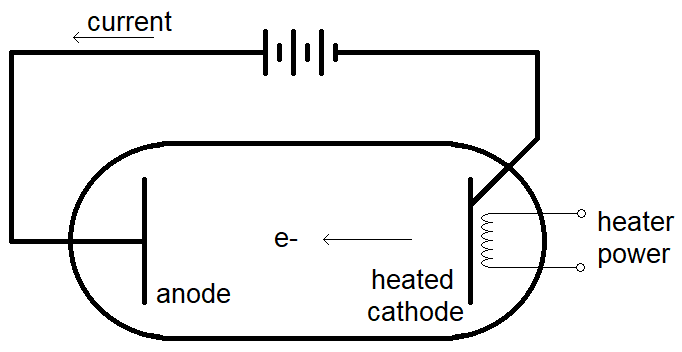
- thermionic valve
- A vacuum tube containing two or more electrodes. Thermionic pertains to the emission of electrons by heat; the cathode is heated to emit free electrons (cathode rays), which are attracted to a positively charged anode, creating a rectified current. A tube with just these two electrodes is a vacuum-tube diode, invented in 1904. The state of the cathode heater – on or off – controls whether the diode passes or blocks current. Unlike a semiconductor diode, it doesn’t allow for reverse bias.
- Add a third electrode (a grid) between anode and cathode, and the device becomes a triode – an amplifier, with voltage to the grid controlling the cathode-anode current. The vacuum-tube triode, invented in 1906, was the fundamental component of amplifiers and oscillators until the advent of the semiconductor transistor. Transistors are cheaper, more rugged, more power-efficient, and, so far, much smaller.
- Vacuum tubes are less vulnerable to heat and radiation. They also have the potential to be faster and handle much higher frequencies, because electrons move more rapidly in a vacuum than in a semiconductor. For this reason, researchers continue to work on nano-vacuum-tube transistors, which are small enough and use low enough voltages that they can dispense with the heated cathode and even with the vacuum. Like solid-state transistors, they use field-effect gate electrodes to control current flow.
- A thyratron is a two-state triode, i.e., a switch, with the grid merely controlling whether current is on or off. A pentode is a thermionic valve with five electrodes. See cathode ray tube (CRT).
- thermistor
- A device with resistance that varies as a function of temperature. More fragile and with a smaller temperature range than a RTD or thermocouple, but more sensitive too.
- thermite
- A powdered alloy, usually Fe2O3 (common red rust) and aluminum. If ignited (at ~2500 K/4000 °F), it burns with intense heat using its own oxygen. Thermite devices contain other compounds to lower ignition temperature and increase heat dispersal.
- thermocouple
- A device with a junction of two different metals producing a voltage that varies as a function of temperature differential between leads and tip. Cheap and rugged, with a very wide temperature range, but poor sensitivity compared to a RTD or thermistor.
- thermodynamics
- The study of change in physical systems, broken down into processes that use and transfer energy. The famous Three Laws of Thermodynamics, preceded by an unofficial zeroth law, boil down to:
- 0) You’re in a game (two systems in thermal equilibrium with a third are in equilibrium with one another).
- 1) You can’t win (matter and energy are conserved, and can’t be created or destroyed).
- 2) You can’t break even (entropy always increases, i.e., no process is 100% efficient).
- 3) You can’t quit (absolute zero, the temperature at which all processes stop, is unattainable).
- Thick Ethernet
- See 802.3.
- Thicknet
- See 802.3.
- thin client
- Also called a network computer, or cloud client computer. A networked PC with minimal hardware, and commonly little or no internal storage. This makes it cheaper, smaller, and more robust than a PC, albeit dependent on a server for all data and applications, potentially including the operating system. It’s meant for single-function roles such as data input, Web browsing, games, and entertainment. Intel’s NUC is a type of thin client.
- See 802.3.
- Thinnet
- See 802.3.
- thread
- A distinct chain of execution within a running process on a computer. Multi-threaded processes share a common memory address space; see mutex.
- threading
- In the US, the threading on a screw or threaded connector is defined by its outer diameter and the number of turns per inch: 4-40, 6-32, 8-32, etc. The first number corresponds to diameter, as follows:
- Most screw sizes come with two different threadings, dubbed “coarse” and “fine”. There are also metric screws, and a British standard that goes, in order of increasing size: 8BA, 6BA, 4BA, 2BA, 0BA. By convention, screw threading follows the right-hand rule unless otherwise stated.
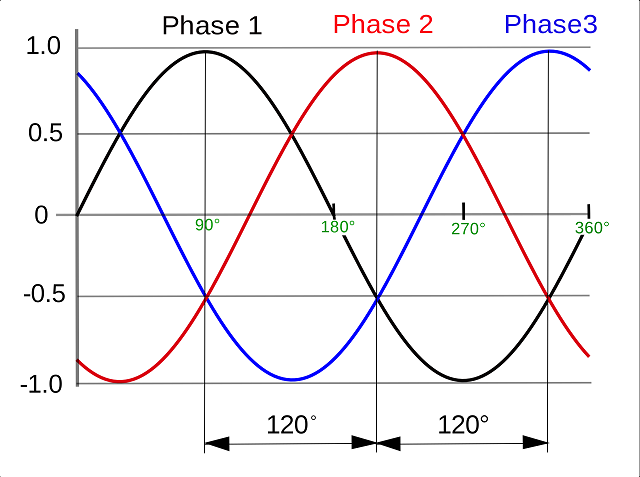
- three-phase
- Most large electrical generators are designed to produce three AC outputs separated by 120° of phase. This is three-phase power. It requires four lines (one for each phase, plus a shared return) throughout the power distribution grid. Single-phase wiring for NEMA standard residential outlets uses just one cable (plus return) from a three-phase distribution line.
- Three-phase motors are used for machinery that needs a higher constant power or smoother motor performance. This requires either a special three-phase outlet drawing on all three hot lines from the grid, or a phase converter. The power engineers who designed our electrical grids settled on three phases because two isn’t adequate for such systems, while four would mean the huge added cost of an additional cable throughout the grid. Three is good enough.
- throttling
- Reducing the bandwidth available to users of a data connection.
- thumb drive
- Also called a USB stick or flash drive, although the latter term can mean a SSD. A small, removable data-storage device with a USB connector, usually Type A. By 2010, these drives had anywhere from 1 to 256 GB of flash memory. By 2011, thumb drives with capacities as large as 2 TB were in development. Compare SD card. Infected thumb drives are a common vector for malware.
- Thunderbolt
- An Intel/Apple serial data bus standard for connecting video monitors and also other peripherals to a computing device. The 2011 Thunderbolt 1 uses mini-DisplayPort (MDP) connectors, with a lightning-bolt icon to distinguish them from DisplayPort graphics connectors. (Thunderbolt supports DisplayPort devices, but DisplayPort does not support Thunderbolt.) It carries up to four PCIe 2.0 signals and a DisplayPort 1.1a signal, supports up to 6 connected devices, and provides DC power for unpowered devices.
- The 2013 Thunderbolt 2 can carry DisplayPort 1.2 and 4K video, and is backward-compatible with Thunderbolt 1.
- The 2016 Thunderbolt 3 uses USB type C connectors, carries USB 3.1 along with two DisplayPort 1.2 signals and four PCIe 3.0 signals, and can handle uncompressed 8K video. It remains backward-compatible with Thunderbolt 1 and 2 if adapter cables are used, and supports USB 3.1 devices, although of course USB type C ports and cables do not support Thunderbolt devices.
- thyratron
- See thermionic valve.
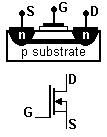
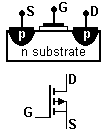
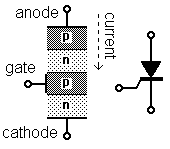
- thyristor
- A semiconductor power switch, the solid-state equivalent of the vacuum-tube thyratron (see thermionic valve). The switch closes when a small gate current is applied or, in two-terminal devices, when breakdown voltage is reached. It can handle very high voltages, which is why it’s used in the electric grid, but it switches more slowly than a transistor. Types:
- diac – From “diode AC”. Functionally, two parallel Zener diodes with opposite direction. When voltage across it in either direction reaches breakdown, it conducts. It thus has only two terminals.
- SCR – Silicon-Controlled Rectifier. A four-layer pnpn device, like a junction transistor with an extra layer. This gives it two forward-biased (hence conducting) pn junctions straddling one reverse-biased np junction. A small current applied to the np junction gate closes the switch, allowing the device to conduct current in one direction only.
- triac – From “triode AC”. Functionally, two parallel SCRs with opposite direction and a single control gate. This means that it will conduct in either direction. It’s common as a switched AC power controller.
- THz
- Terahertz. 1012 hertz. See also RF.
- TI
- Texas Instruments. A big manufacturer of electronics components, including the TMS320 series of DSP chips, and the CCS (Code Composer Studio) IDE.
- TIA
- Telecommunications Industry Association. An ANSI-accredited standards group that grew out of EIA.
- TIFF
- Tagged Image File Format. A graphics standard originally for fax images, also abbreviated TIF. The usual filename extension is .tif.
- TIG
- Tungsten Inert Gas. A welding technology that uses a non-melting tungsten electrode surrounded by a jet of a non-reactive gas to generate an electrical welding arc. Also called gas tungsten arc welding (GTAW).
- TIP
- Texas Instruments Power. The part-number prefix for an old family of power transistors made by Texas Instruments in the JEDEC standard TO-## form factor.
- TIR
- Total Internal Reflection. The phenomenon that causes light to propagate down a fiber-optic cable.
- A material’s index of refraction is the ratio of the speed of a light in a vacuum to its speed in the material. At the boundary of two media with indices of refraction n1 and n2, the angle of incidence θ1 determines the angle of refraction θ2 in accordance with Snell’s Law: n1 sin [θ1] = n2 sin [θ2].
- If n2 < n1, then at any angle of incidence θ1 such that sin [θ2] would be greater than 1 (an impossibility), the incident ray is entirely reflected. This is TIR. In a fiber-optic cable, the cladding therefore has a lower index of refraction than the core.
- TLC
- Three-Level Cell. See flash memory.
- TLD
- Top Level Domain. The last part of an Internet address name, such as .com, .edu, or .org. See DNS.
- TL;DR
- Too Long; Didn’t Read. A textspeak comment that is sometimes used online as the header for a summary of an article or other document.
- TLE
- Transient Luminous Event. Any of several little-understood, upper-atmosphere photoelectric effects associated with storm clouds or lightning. Recognized types include the blue jet, which shoots up from cloud tops; the red sprite, which shoots down from the ionosphere; and the ELVES (Emissions of Light and Very low frequency perturbations due to Electromagnetic pulse Sources), which radiates into the ionosphere and lasts less than a millisecond.
- TLP
- Transmission Line Pulse. A method for testing the tolerance of circuits to ESD. It uses charge from a floating cable to approximate the shock delivered by the JEDEC standard ESD models, and applies time-domain reflectometry (TDR) to analyze the target’s response. Very Fast TLP (VF-TLP) is a newer technique using shorter pulses with faster rise times.
- TLS
- Transport Layer Security. A Web protocol for implementing encryption, introduced in 1999, that has gradually replaced the similar but less secure SSL. TLS 1.2 was released in 2008, and TLS 1.3 in 2018. It runs in the network layer of the OSI model and makes calls to TCP/IP protocols on behalf of application-layer protocols such as HTTP. Servers send TLS page data through TCP/IP port 443 instead of port 80, the HTTP port.
- TLS lets servers and clients authenticate themselves to one another and establish encrypted connections with digital certificates issued by a mutually recognized Certificate Authority (CA), using a system known as a public key infrastructure (PKI). A certificate includes a public encryption key made available to clients, and a private encryption key held only by the encrypted server. When a client accesses the server, it first receives the public key and some other information, and contacts the issuing CA to verify the key. If verification succeeds, the client creates an initial private session key, encrypts it with the public key, and sends it to the server. The client and server both perform the same steps on this initial key to generate a second session key, which they use to encrypt and decrypt all further communication using one of the TLS-supported asymmetric encryption algorithms, commonly RSA or D-H. This scheme is proof against standard man in the middle attacks so long as the CA itself is not compromised, but has other, complex vulnerabilities.
- Any site wanting to provide TLS-encrypted connections must obtain a license and certificate from a CA. There are hundreds of CAs, each potentially issuing many unique certificates. Modern browsers, operating systems, and other applications come pre-loaded with a list of trusted CAs. (In Firefox 37, select “Tools - Options” from the menu bar; in the Options window, select Advanced, select the Certificates tab, and click “View Certificates”. In Chrome 41, select “Settings” from the menu, click “Show advanced settings...” at the bottom, scroll down to HTTPS/SSL, and click “Manage certificates...”; in the Certificates window, select the Trusted Root Certification Authorities tab.) Users can add certificates to this list. A certificate downloads as a file in one of several encoding formats: DER (binary format), PEM (base64 ASCII format), P7B/PKCS#7 (also ASCII), or PFX/PKCS#12 (binary with private key). The filename extension will usually be .crt, .cer, or .key, or something that indicates the specific encoding format such as .pem, .der, .p7b, or .pfx.
- By convention, URLs that employ TLS start with
https:instead ofhttp:. However, browsers often default to hiding this part of the URL. In Firefox 37, restore display of the full URL by enteringabout:configin the URL bar, finding the configuration line called browser.urlbar.trimURLs, and double-clicking it to change its setting from true to false. Browsers usually display a padlock icon next to the URL to indicate TLS is in use, although Google Chrome is switching (2021) to instead displaying warning indicators for sites that aren’t secured. Bear in mind that the use of TLS does not mean that the Web site itself is safe or legitimate. Phishing sites frequently have TLS because it encourages trust. - TMDS
- Transition Minimized Differential Signaling. A high-speed serial data encoding format, meant to run on twisted-pair cable. It was created to carry digital video signals, notably DVI and HDMI.
- TMR
- Tunnel Magneto-Resistance. The same thing as GMR, except that it relies on a non-metallic insulating barrier, e.g., Al2O3 or MgO. The TMR effect became the standard mechanism for hard disk drive read heads around 2006. See also MRAM.
- TMS
- Test Mode Select. The JTAG bus signal line that triggers state changes.
- TMS320
- A family of Texas Instruments DSP chip architectures dating to 1983. Some sub-families:
- TMS320C80 – (1995) RISC microprocessor combining parallel processing and DSP.
- TMS320C54xx – (1995) C5000 series. Low cost, low power, common in cell phones.
- TMS320C55xx – (2000) C5000 series. Successor to the 320C54xx.
- TMS320C6x – The C6000 series, using VLIW processing. Members include the TMS320C62x (1997), TMS320C64x (2000), TMS320C67x, and TMS320C674x.
- TNC
- See cable connector.
- TNR
- Transmit Not Ready.
- TNT
- (1)
- Trinitrotoluene. A toxic but stable explosive compound, C6H2(NO2)3CH3, invented in 1863 by Swedish chemist and engineer Alfred Nobel and still in wide use. A-bomb and H-bomb explosions are ranked by their equivalence to metric tons (T), kilotons (kT), or megatons (MT) of TNT.
- (2)
- See cable connector.
- TO-##
- Transistor Outline. A standard JEDEC form factor, primarily for transistors.
- tokamak
- From the Russian токамак, an acronym of a description of the hardware. A toroidal device that generates ionized, super-heated gas (plasma) and confines it within a magnetic field. It’s the most common basis for research on controlled nuclear fusion.
- token bus
- An old LAN technology, still (2005) used in ARCnet. The server continually circulates empty message frames on the LAN bus. Any node that wants to send inserts a variable-length token and a message into an empty frame, and transmits it. The destination node clears the token and message after reading, freeing the frame for re-use.
- token ring
- A largely obsolete IEEE 802.5 network in which devices are connected in a virtual ring, with a digital token passed around. Only the device with the token can transmit. A network packet contains up to 17 kB of data plus a few bytes (20 is typical) of addressing and overhead info. The network runs at 4 Mb/s and uses a thick, shielded, 2-pair cable with IBM data connectors (IDCs). See MSAU.
- Tor
- The Onion Router, originally. As of 2015, Tor is the most popular darknet. “Onion” refers to the network’s layered approach to anonymity, by which users are routed through a chain of three or more anonymizing proxy servers in different geographical regions, so that tracing a communication back to its source requires (in theory, anyway) compromising all of them. Tor URLs are randomly generated, and end with the .onion TLD. As of September 2015, the IANA lists .onion as a special-use domain to support use of SSL or TLS certificates by Tor sites.
- Tor was released in 2002 as a US Naval Research Laboratory (NRL) project. Since 2006, an EFF-sponsored non-profit corporation called The Tor Project (www.torproject.org) maintains and distributes the Tor Browser software that users must have to access the network. (Other organizations also develop Tor browsers.)
- Because the network has no core infrastructure, it depends on support from users running servers that act as proxies for other users. Data (e-mail, Web queries, Web responses, etc.) sent over the network is encrypted by the originating user’s browser using the public key of the last proxy in a randomly selected chain. This means that the first proxy in the chain (the entry node) can see who the user is, but not what the data is; the last proxy (the exit node), because it performs the final decryption, can see what the data is, but not who sent it; and the proxies in between (the middle nodes) don’t know either one. Exit nodes are the point of contact between Tor and the public Internet, so they’re the most likely targets for hackers, lawsuits, and governments.
- ToS
- Terms of Service. A set of rules that an ISP, Web-based service provider, online game, etc. requires users to follow.
- TOSA
- Transmitter Optical Sub-Assembly. A device that provides a transmit interface to a fiber line. See ROSA.
- TOSLINK
- Toshiba Link. A family of fiber-optic connections developed by Toshiba, and mainly used for digital sound. Usually employs the F05 fiber-optic connector, the port for which resembles a tiny dog door. See also SPDIF.
- totem pole
- A TTL circuit output with a bipolar configuration. As the resistance of one of its active devices increases, that of the other decreases. It’s equivalent to a push-pull output, but only for 0V and 5V states, and it can’t source or sink as much current.
- TPM
- (1)
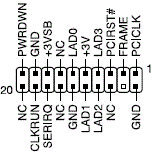
- Trusted Platform Module. Specification for an independent microprocessor built into a PC or other device to implement Trusted Computing, which includes security-checking the boot process. Since 2006-2007, motherboards are available with either a SMT pad for a soldered TPM chip, or a LPC header for a removable TPM. (The image below is an example – actual pin count varies.)
- The module or chip itself is commonly installed on systems sold to business or government (the US Department of Defense requires it), but not on those for private use. The default BIOS setting usually leaves an installed TPM disabled. However, this is up to the BIOS vendor and/or the system vendor, and Windows 8 is said to enable it automatically. Windows RT requires an enabled TPM, as do some network authentication and hard-drive encryption programs. Windows 11, expected in late 2021, will require TPM as well.
- (2)
- Technological Protection Measure. See digital lock.
- TPMS
- Tire Pressure Monitoring System. Air pressure sensors with short-range wireless transmitters, mounted in vehicle tires. They transmit (mostly in the 315-433 MHz range) at intervals or upon request to the vehicle computer. Each tire uses a unique ID. Mandated by the National Highway Traffic Safety Administration for all new US vehicles starting September 2007, TPMS is, like other uses of RFID, seen as a privacy threat: roadside sensors could use it to identify the owners of passing vehicles.
- TPS
- Third-Person Shooter. Any of the class of combat video games in which the player controls one character and sees events from a perspective that shows the character. Some games can switch between TPS and FPS.
- TPU
- Tensor Processing Unit. A specialized microprocessor developed by Google, starting about 2014, specifically for the machine learning tasks of artificial neural networks. It runs inference-stage algorithms much faster and with much less power than CPUs or even FPGAs, in part by taking advantage of the reduced need for precision in such algorithms.
- TPV
- Thermo-Photovoltaic. See PV.
- TQFP
- Thin Quad Flat Pack. See JEDEC.
- T-RAM
- Thyristor Random Access Memory. A volatile memory technology announced in 2009, claimed to have the density of DRAM with the speed of SRAM. Its uses and prospects remain unclear. Compare Z-RAM.
- transceiver
- Transmitter/Receiver. A device that both transmits and receives. It can be an RF device, or a fiber-optic or electrical device on a transmission line.
- transducer
- A device that converts energy from one form to another, e.g. an antenna (EM waves to electric current, and vice-versa) or a solenoid (electric current to mechanical motion), a lightbulb (electric current to light and heat), etc.
- transfer function
- A mathematical expression that describes a circuit’s output as a function of input.
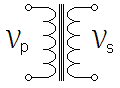
- transformer
- A device to transfer power from one circuit to another, usually with a change in voltage level. It consists of a primary inductor coil and one or more secondary coils wound about a single core. Alternating current in the primary creates an alternating magnetic field centered in the core, which in turn induces AC in the secondary. This is called mutual inductance. The ratio of primary to secondary windings determines whether a transformer steps voltage up, or down, or neither.
- An isolation transformer, for example, has the same number of turns in each coil, since its purpose is simply to decouple the two circuits that it connects, blocking DC and ground-loop currents. In a power transformer, the coil with fewer turns (and, typically, thicker wire) has lower voltage and higher current in direct proportion to the ratio of primary to secondary windings. Voltages across the primary and secondary coils are denoted vp and vs; currents through the coils are ip and is.
- The step-down transformers used by power companies exceed 98% efficiency with a solid core and liquid coolant – originally PCB, but nowadays a non-toxic fluorinated hydrocarbon. This insulating oil produces a flammable vapor. Overheating due to line troubles or a lightning strike can cause electrical discharge through bubbles in the oil, producing an explosion.
- transistor
- From “transfer resistor”. A three-terminal, solid-state electronic device invented in 1947 that typically serves as either an amplifier or a switch. It replaced many older devices based on the principle of the thermionic valve (vacuum tube). The digital logic now ubiquitous in electronics relies on dense arrays of transistors.
- A transistor’s performance is dictated partly by its construction, and partly by the semiconductor materials used to build it. The properties of semiconductors are adjusted by doping to make them either positive (p-type electron acceptors) or negative (n-type electron donors). There are two basic classes of transistor: the older bipolar junction transistor (BJT), and the newer field effect transistor (FET), which is unipolar.
- Bipolar Junction Transistor (BJT)
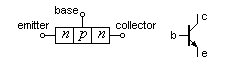
- A junction transistor consists of either two p-type semiconductor materials separated by an n-type material (the pnp), or two n-types separated by a p-type (the npn), as shown below. (The drawings show a simplified model, not a physically accurate layout.) The middle layer is the base, and the other two are the collector and emitter. The emitter is more heavily doped than the base, and the collector more lightly doped. The BJT is called bipolar because it uses both positive and negative charge carriers. A negative charge carrier is, of course, an electron. A positive charge carrier, referred to as a hole, is simply the absence of an electron. At the physical level, it’s the electrons that actually move, but the engineering math still works when holes are treated as moving positive charges.
- When a BJT is used as an amplifying element, the base-to-emitter junction is in a forward-biased (conducting) condition, and the base-to-collector junction is reverse-biased or non-conducting. The device is controlled by current input to the base: a small change in the input base-to-emitter current causes either holes (for pnp devices) or electrons (for npn) to flow from the emitter to the base. Most then flow into the collector, amplifying the input. Gain is collector current over base current.
- The heterojunction bipolar transistor (HBT) uses different materials with different energy bandgaps for the emitter, base, and/or collector, making it extremely fast. It’s common in power amplifiers.
- Field Effect Transistor (FET)
- The FET is unipolar in that, in contrast to the BJT, it uses electrons or holes but not both. It has two terminals called the source and the drain, a channel of charge-donor dielectric connecting them, and a charge-accepting dielectric called the gate (with its own gate terminal) adjacent to the channel. Voltage applied to the gate controls the current flow between source and drain by depleting the donor region of its charge carriers, pinching off the channel. This is the eponymous field effect. Little or no current flows through the gate, so the FET is a voltage-controlled device, and uses less power than the BJT. Major types of FET, in roughly chronological order:
- JFET – Junction Field-Effect Transistor. Also now called a planar or 2-D FET to distinguish it from 3-D layouts such as the FinFET and GAAFET, which can support much smaller feature size. This is the simplest FET, with a p- or n-doped channel connecting the drain and source, and the gate (with opposite doping) forming a PN junction along the edges of the channel. Changing the gate-to-source voltage VGS changes the current flow by enlarging or narrowing the channel. Decreasing VGS stops n-channel flow, and increasing it stops a p-channel. JFETs require little gate current, but have only modest gain.
- MOSFET – Metal-Oxide-Semiconductor Field-Effect Transistor. Also called insulated gate field effect transistor (IGFET). The depletion-mode MOSFET is similar to the JFET, but the conducting channel is insulated from the opposite-doped gate terminal (once aluminum, now silicon) by a layer of SiO2. This means that the gate, in theory, conducts no current even under reverse voltage – although as transistors became smaller and gate oxide layers shrank to just a few atoms thick, they started to leak quantum tunneling current, underscoring the need for new transistor designs. The enhancement-mode MOSFET lacks a doped channel from drain to source, relying on the gate voltage to create a channel. As of 2014, all commercial MOSFETs were silicon-based.
- MESFET – Metal-Semiconductor Field-Effect Transistor. Similar to the JFET, but the carrier flow from source to drain is controlled through a metal or polysilicon Schottky gate instead of a pn junction gate. Varying the depletion layer width underneath the gate modulates the thickness of the conducting channel, and thereby controls the current. The key advantage of the MESFET is its greater switching speed, due to the higher mobility of carriers in the channel as compared to the MOSFET. It’s made with InP or GaAs, not silicon, which makes it expensive.
- IGBT – Insulated Gate Bipolar Transistor. Also called Insulated Gate Transistor (IGT). A power switch that combines the low power drive characteristics of the MOSFET with the low conduction losses and high blocking voltage characteristics of the BJT. It lacks the MOSFET’s switching speed, but handles voltages (above 300V) and currents that a silicon MOSFET can’t. MOSFETs made with semiconductors that have a wider bandgap than silicon are expected to replace the IGBT.
- HEMT – High Electron Mobility Transistor. A MESFET whose channel is the junction between two materials with differing bandgaps. This heterojunction is an induced, two-dimensional quantum well in which electrons are highly mobile, permitting a very fast transistor. As of 2022, researchers have pushed HEMTs to frequencies in excess of 1 THz. The two materials must have the same lattice constant to fit together, although the P-HEMT is based on breaking this rule.
- P-HEMT – Pseudomorphic HEMT. This variant of the HEMT uses two materials with very different bandgap energies, permitting even higher switching speeds. They also have very different lattice constants. However, using just a very thin layer of one material permits its lattice to stretch so that it fits the other, creating the two-dimensional pseudomorphic heterojunction. The P-HEMT, like its bipolar cousin the HBT, is common in power amplifiers.
- E-pHEMT – Enhancement mode Pseudomorphic HEMT. Using enhancement mode rather than depletion mode, so that it doesn’t conduct at zero gate bias.
- OFET – Organic Field-Effect Transistor. Made from organic semiconducting polymers on a flexible plastic substrate. OFETs can’t approach the speed, efficiency, and density of other FET types, but their flexibility and durability are valuable for mobile and wearable devices, and they’re a good fit with the all-plastic, active-matrix backplanes of OLED displays.
- FinFET – Fin Field-Effect Transistor. A three-dimensional MOSFET, making its commercial debut in 2011 on Intel chips with 22 nm feature size, and later reaching its limits at 7 nm feature size. Its source-to-drain channel is a fin projecting above the substrate, with the gate wrapping around it. While trickier to manufacture than conventional planar (2-D) transistors at the same scale, it can carry higher current with less loss, so it performs better at the ever-smaller feature sizes used for new CPU chips.
- TFET – Tunneling Field Effect Transistor. As feature size shrinks, devices exhibit undesirable leak currents due to quantum tunneling of electrons across nanometer-scale barriers. Instead of fighting it, the TFET exploits this effect to create device state: its gate voltage controls the likelihood of source-to-drain quantum tunneling. The behavior is therefore the same as a standard FET, but depends on a different mechanism, requires lower gate voltages to achieve, and works at smaller feature sizes. An obstacle to this technology is that the most common semiconductors, silicon and germanium, have weak tunneling-current gain.
- GAAFET – Gate-All-Around FET. Also called a nanowire or nanosheet FET, in R&D as of 2014. An approach that permits still smaller feature size: the current channel is a set of very thin wires or sheets of conducting material passing through a gate plane between source & drain. Because the gate material surrounds every wire or sheet, with a thin insulating layer of dielectric between them to block leak currents, applied gate voltage pinches off source-to-drain current. Multiple conductors are necessary because they’re too thin for one to carry enough current. Conductors in the form of sheets (strips) provide better performance than wires, because the tiny diameter of the wires imposes too tight a limit on switching speed and current. Fettucine rather than spaghetti.
- QWFET – Quantum Well Field-Effect Transistor. Similar to the finFET, but able to operate at even lower power.
- VTFET – Vertical Transport Field-Effect Transistor. An IBM/Samsung design in R&D as of 2021 to allow vertical stacking of the transistors, shortening the interconnects between them.
- RibbonFET – The type of GAAFET that uses strips rather than wires for the conducting channel.
- The most common semiconductor material is crystalline silicon, with other crystals for special applications. Still in R&D are polymer (i.e. plastic) transistors, which suffer from poor charge mobility; graphene, cut into quantum dots with odd electrical properties (see spin); carbon nanotube FETs, hard to fabricate but lightweight, fast, and highly resistant to heat & radiation; and single-molecule transistors of hydrogen, carbon, and sulfur. In 2010, experimental graphene transistors reached 100 GHz.
- As it becomes ever more difficult to build transistors with smaller feature size, some researchers are focusing on the technology that semiconductor transistors replaced: the vacuum tube, shrunk to nanoscale. These devices have potential to operate into the terahertz frequency range; see thermionic valve.
- transmission line
- Every line for carrying electrical signals has at least two conductors. In unbalanced lines, these are a signal path and a grounded return. The earliest lines used an earth return as the second conductor (see telegraph). Balanced lines have two ungrounded signal wires and reference the differential between them. Stranded-wire lines are more flexible than solid-wire, but have slightly higher attenuation.
- transponder
- Transmitter/Responder. A transceiver that transmits only in response to a querying signal, or a passive device that simply reflects a signal or produces a detectable change in a magnetic or electric field. Many aircraft have RF transponders to identify them to ground controllers.
- trellis code
- See TCM.
- triac
- From “triode AC”. See thyristor.
- triaxial
- Similar to coaxial cable, but a triax cable has three conductors – a signal, a return, and an outer shield. If the grounded shield carries no signal, the cable has much higher SNR than coax. Some oddball applications of triax do use the shield to carry a signal. Triaxial cable commonly uses triax or TNT cable connectors, which are based on the BNC and TNC connectors respectively.
- triboelectric
- Refers to the process by which electric charge migrates between complementary materials in contact with one another, creating the charge differential responsible for static electricity. Triboelectric generators can produce small amounts of useable power, enough to run microelectronics.
- trigonometry
- Given a right triangle, the six possible relations between its sides for either of its acute angles are sine = opposite/hypotenuse, cosine = adjacent/hypotenuse, tangent = opposite/adjacent, cotangent = adjacent/opposite, secant = hypotenuse/adjacent, and cosecant = hypotenuse/opposite.
- The inverse functions – arcsin, arccos, arctan, arccot, arcsec, and arccsc – are often denoted by the superscript -1, e.g. arcsin(x) = sin-1(x). This is confusing, because these functions are not the multiplicative inverses – they’re reversals of the original operations. For example, sin(45°) ≈ 0.7071, so arcsin(0.7071) ≈ 45°. They’re also abbreviated as asin, acos, atan, acot, asec, and acsc.
- Generalize the case of the right triangle to a vector on the unit circle, i.e., radius normalized to 1. A positive angle θ is counter-clockwise rotation from the positive x-axis, so, unlike in a right triangle, it can pass 90°. The adjacent and opposite sides – the cosine and sine of θ – are, respectively, the vector’s projection on the abscissa (x-axis) and ordinate (y-axis). Tangent and cotangent have a period of 180° (π radians), while the others have period 360° (2π radians).
- triode
- See thermionic valve.
- trojan
- See malware.
- troll
- The term began as an analogy to fishing with baited lines, but most people, for obvious reasons, associate it with the nasty fairy-tale creature that lives under a bridge. Originally, a troll was just an Internet posting likely to draw angry responses or start an argument, or a person who posted such things, be it out of ignorance, mischief, malice, didacticism, ego, or simply to generate click bait. The meaning has expanded to include anyone who engages in disruptive, harassing, threatening, or abusive online behavior. (For patent trolls, see NPE.) Some sub-categories of modern trolling:
- doxing – Publishing personal data (contact information, home address, workplace, family, etc.) about an individual to make that person a target of online abuse or, in extreme cases, in-person harassment, threats, and attacks.
- freeping – From Free Republic, a far-right Web forum. Rallying like-minded trolls to change the outcome of a poll, survey, or vote, the content of a discussion, or even the membership of an organization.
- oppo – Short for “opposition research”, a term from political campaigning. Digging into someone’s online data trail to find and publicize damaging or embarrassing information.
- sealioning – From a 2014 webcomic that illustrated the tactic using sea lions as the hot-button topic, this means harassing someone with relentless, pseudo-polite offers to engage in public debate about their views. The goal is harassment and provocation, not debate.
- sock puppet – A false online identity created by a troll as a means to provoke or manipulate others.
- swatting – Triggering a police SWAT team raid on a location by making a false report of a crime.
- tropic
- If you draw a line from the center of the Sun to the center of the Earth, the point where it intersects Earth’s surface is always between 23° 27' north and 23° 27' south. These latitudes are the Tropic of Cancer and the Tropic of Capricorn, respectively. See Earth.
- TRS
- Tip Ring Sleeve. The most common version of the jack plug, or phone plug/jack, an old standard for single-pin audio signal connectors. The female jack accepts a male plug of the same diameter, which has one or more insulating rings. One ring divides the plug into two separate contact regions, making it a mono or tip-sleeve (TS) plug; two rings, hence three regions, make it a stereo or tip-ring-sleeve (TRS) plug; three rings is a tip-ring-ring-sleeve (TRRS) for carrying three signals plus ground. The terms come from telephone wiring, one of the first uses for these plugs.
- The original 1/4" (6.35mm) plug dates from 1878, and is becoming rare in consumer electronics. The 2.5 mm (3/32") and 3.5 mm (1/8") types are much more common. These connectors are sometimes used for DC power input.
- TRS-80
- Tandy Radio Shack 80. A popular line of PCs that Radio Shack introduced in 1977, semi-affectionately called “Trash-80” by users. The Model I had a 1.77 MHz Zilog Z-80A CPU, 4 kB (later 16 kB) of RAM, and a 12-inch, 16 × 64 character monochrome display. Its OS was a version of BASIC, and its data output was a cassette tape recorder. The family continued into the mid-1980s.
- TRST
- TAP (Test Access Port) Reset. The optional reset line for JTAG bus state.
- Trusted Computing
- A security initiative by the PC industry’s Trusted Computing Group (TCG) to implement Secure Boot: a security process that uses 2048-bit public-key encryption, implemented by a UEFI running from a TPM, to prevent CPUs from loading unauthorized software and files. The main selling point for this technology is that it can secure the system against malware. Its obvious shortcoming is that it can also secure the system against its user, because a handful of large corporations will define what’s authorized and what’s not, and they have not only the ability but a financial incentive to block certain files, software, Internet domains, sites, etc.
- Online interaction in a Trusted Computing framework attempts to preserve user anonymity by having a trusted third party (TTP) relay authentication. Again, unwarranted trust is the issue.
- T/s
- Transfers per second. An alternative way of defining data rate: by the number of data transfer operations per second rather than the more usual bits per second. Like samples/second or symbols/second, this terminology exists because some systems can have different settings for the number of bits in each operation. The usual extensions – 103 T/s = 1 kT/s, 103 kT/s = 1 MT/s, 103 MT/s = 1 GT/s, etc. – still apply.
- TS
- Tip Sleeve. See TRS.
- TSMC
- Taiwan Semiconductor Manufacturing Company. Still the world’s largest IC foundry as of 2022.
- TSP
- TAPI Service Provider. See API.
- TSR
- Terminate and Stay Resident. The MS-DOS version of a daemon: any process started by the system, e.g.
COMMAND.COM, and permanently resident in main memory waiting to be called. - TSSOP
- Thin Shrink Small Outline Package. See JEDEC.
- TSV
- Through-Silicon Via. See via.
- TTL
- (1)
- Transistor-Transistor Logic. See logic family.
- (2)
- Time To Live. In network protocols, a scheme to prevent endless forwarding of undeliverable data packets. Each datagram has a TTL field (in IPv4, the 9th byte of the 20-byte packet header; in IPv6, it’s called hop limit instead), and each router that it passes through decrements the field. If the field reaches 0, the router will not forward the packet, but will send an ICMP error packet back to the source. Under the DNS, TTL is the number of seconds that a server will cache a resource record (IP address, mailbox, host hardware & OS, etc.) before having to re-verify it.
- TTY
- From “teletype”. Often written in lower case, tty. Refers to the old teletype printers, data signals compatible with them, and terminal-emulation programs that can display their data on monitors.
- turbo code
- Named after turbocharging engines, which use their own exhaust to force air into the engine and boost combustion. This important convolutional FEC code technique was discovered in 1993. It comes within 0.5 dB or less of the Shannon channel limit with a BER of 10-5, but has a large decoding delay and performs poorly where lower BER is desired.
- Implementations use two parallel encoders, one working with an interleaved version of the data, to produce very long codewords (~1000 bits) consisting of the original data plus two blocks of FEC bits. At the destination are two decoders, one for each FEC block. The one working on the interleaved-data FEC gets an identically interleaved version of the received data. They generate confidence level values for each bit and iteratively compare and refine their results until they agree. Turbo code, along with LDPC, constitutes a new, third class of FEC called iterative codes.
- Turing machine
- British mathematician Alan Turing’s 1936 theoretical model, which he called a Universal Machine, of a simple state machine capable of handling any conceivable computation. The model consists of a set of data cells (conceived as a paper tape of unbounded length but using a finite symbol set); an active head that can read any cell and optionally write a change to it; the machine state, defined by data read and changes written as one of a finite set of states; and a set of transitions (operating rules) that determine, for any combination of state and current input, what the machine will do next.
- There are six fundamental operations the machine must be able to perform: read, write, move left one cell, move right one cell, change state, and halt. A computing device is Turing-equivalent if it has these capabilities, or their equivalents – obviously, random-access memory (RAM) goes beyond move-one-cell operations. Turing complete refers to a programming language that can implement all the operations of a Turing machine.
- Turing test
- An attempt to distinguish a human being from an algorithm through conversation when all interaction is electronic. Modern AI models can pass easily. The Winograd schema, an intentionally ambiguous statement that a human uses analytical understanding and common sense to resolve, is more effective, but AI can be designed to pass it as well without achieving these qualities.
- The CAPTCHA and DCG are reverse Turing tests, in which a machine rather than a human makes the determination.
- turnkey system
- A complete system, including hardware and software, assembled and installed by a vendor and sold as a total package. You turn the key, and you’re operational.
- TV
- Television. See ATSC, DTV, NTSC, PAL, SECAM.
- TVRO
- Television Receive-Only. Old type of satellite TV system. See BUD.
- TVS
- (1)
- Transient Voltage Surge.
- (2)
- Transient Voltage Suppressor. A component, typically a varistor or Zener diode, that protects a circuit from high-voltage transients by shunting the overvoltage to ground.
- twinax
- A shielded twisted pair cable with its grounded shielding braid separated from the wires by a dielectric to minimize leakage capacitance to ground. Very lossy above about 15 MHz. Also refers to a standard two-pin twinax cable connector, with ¾"-20 threaded coupling.
- two-packed
- Computer data stored as two separate values in one memory word. BCD is an example. So is a program storing pairs of 16-bit numbers in a 32-bit array. Beware endianness.
- twos complement
- A way of digitally storing and manipulating signed binary numbers. The most significant bit is actually the sign bit, with 0 meaning positive and 1 negative. One byte can express any value from 127 to -128. To generate a negative number, take its positive equivalent, invert every bit, and add 1. For example, 01111111 is 127, so 10000001 is -127, and 10000000 is -128. Compare ones complement. Twos comp addition is performed with a carry to the next most significant bit, discarding carry from the MSb.
- TWR
- Traveling Wave Reactor. See reactor.
- TWTA
- Traveling Wave Tube Amplifier. A high-gain, low-noise, wide-band, nonlinear microwave amplifier that uses linear pre- and post-filtering. A heated-cathode electron gun sends a beam through a vacuum tube made of some non-ferrous material (not glass!), with magnets on the tube narrowing and focusing the beam. A signal-carrying wire is wrapped around this tube in a helix, with a radius and pitch chosen to ensure that the signal moves along the tube at the same speed as the electron beam. An RF signal input to the helical wire velocity-modulates the electrons in the beam. The resultant bunching of electrons in the beam amplifies the RF signal, which amplifies the beam modulation, and so on, producing exponential amplification of the RF across a wide bandwidth.
- TWTAs are still (2016) the standard way to generate modulated RF with high power and frequency. Early models suffered from poor efficiency. Modern ones have a collector stage to recover most of the electron beam’s energy, resulting in power efficiencies above 65%. A cold-cathode design, the long-time goal of TWTA researchers, would be both more efficient and more durable, but is very hard to achieve at the necessary power levels and frequencies.
- TXT
- (1)
- Trusted Execution Technology. Intel hardware technology to implement so-called Trusted Computing.
- (2)
- Refers to an ASCII-format text file, which will normally have the .txt filename extension.
- TYMNET
- An international commercial computer network used from 1971 to 2004. It began in 1964 as Tymshare, a company that sold dial-up access time on computers.




| #1 = 1/16" | #4 = 7/64" | #8 = 5/32" | #11 = 13/64" | #14 = ¼" | #20 = 5/16" |
| #2 = 5/64" | #5 = 1/8" | #9 = 11/64" | #12 = 7/32" | #16 = 17/64" | #24 = 3/8" |
| #3 = 3/32" | #6 = 9/64" | #10 = 3/16" | #13 = 15/64" | #18 = 19/64" |





Structure and schematic symbol for three types of thyristor