- M#
- For the M1, M2, and M3 microprocessors, see Cyrix.
- M.2
- (2014) Based on mini-SATA and SATA Express, and originally called NGFF (Next Generation Form Factor), this is a physical connector designed to support a SATA, PCIe, or USB connection. It’s the usual form factor for the PCIe-based NVMe interface. It shows up on desktop motherboards as well as in mobile devices, and is a common interface for SSDs.
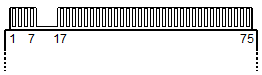
- The M.2 header slot is 22 mm long, and offers 75 contact positions at 0.5 mm spacing: 38 on the odd-numbered side, 37 (offset) on the even-numbered side. Unlike most expansion slots, M.2 requires the edge-connector card to plug in parallel to the surface of the board, with the odd-numbered (A) side facing up. Its header is no more than 3.2 mm high, leaving just 1.47 mm between card connector and board. Standard card size for a SSD is 2242 (22 × 42 mm), 2260 (22 × 60 mm), or 2280 (22 × 80 mm). Most motherboard slots accept more than one size.
- There are different key types for different applications, designated key ID A, B, C, etc. Each notches out some of the 75 contact positions, and no key uses more than 67 of them. A slot or card can be wired for more than one kind of interface, but that’s up to the manufacturer. The slot’s keying should physically block insertion of M.2 devices that use a bus the slot doesn’t have.
- M2M
- Machine To Machine. Refers to communication between devices.
- MAC
- (1)
- Medium Access Control. A unique 6-byte serial number burned into every network-capable device (i.e. stored in a PROM or flash memory chip) at manufacture. Also called the physical address, it’s usually displayed as six hexadecimal values separated by colons, e.g.
90:49:FA:3E:21:25. Most network devices rely on MAC numbers, not IP addresses (layer 2 rather than layer 3 of the OSI model). On a Windows PC, enteringipconfig /allorarp -ain the command window shows both types of address. - Each manufacturer applies to the IEEE Registration Authority for blocks of MAC numbers. The first three bytes are the Organizationally Unique Identifier (OUI), indicating the manufacturer. The name also refers to the MAC protocol, used by CSMA/CD.
- (2)
- Multiplier-Accumulator. A fundamental component of microprocessor and DSP chips. A multiply-accumulate operation multiplies vectors and sums the result.
- Mach
- Named for Austrian physicist Ernst Mach (1838-1916), Mach number is the ratio of an object’s speed to the speed of sound in air at sea level, which is approximately 340 m/s, or 1225 kph (761 mph in US statute miles). The speed of sound varies with pressure, temperature, and humidity. At 6096 m (20,000 feet) ASL, it drops to about 295 m/s, or 1062 kph (660 mph).
- machine learning
- The branch of computer science dealing with algorithms that improve their accuracy at classifying data or predicting outcomes by being trained on data sets that include known-correct classifications or predictions. By processing this training data, the algorithm determines the relative importance of each component of the data to making accurate classifications or predictions for this particular type of data, and weights the components accordingly when analyzing new data.
- Deep learning is a category of machine learning for handling more complex data.
- Mac OS
- Macintosh Operating System. Any of the GUI operating systems used for Apple PCs over the years, starting (1984) with the original Macintosh OS. It ran on Motorola 68k processors, as did its successors System 7.1, System 7.5, Mac OS 7.6, et. al., up through Mac OS 8.1. Mac OS 9 (1999), the final version of the classic Mac OS, dropped the 68k series for PowerPC CPUs, shutting out Macintosh clone-makers. Mac OS X (2001) drew heavily on the Unix-derived NeXTSTEP OS, had a snazzier desktop, and initially ran only on the PowerPC G3, G4, and G5. Apple later added support for x86 processors, which let the clone (“Hackintosh”) makers back in. Starting with version 10.6 (2008), Mac OS X is compatible only with x86 processors. In 2016, Apple changed the name to the annoyingly trendy macOS.
- macro
- This has two distantly related meanings:
- (1)
- At the source-coding level, an identifier that’s mapped to some piece of code, be it a mere object (e.g. a number) or a function-like operation. The compiler substitutes this code snippet for each instance of the macro name. Use of a macro allows the programmer to change just one thing – the macro definition – and modify program behavior everywhere the macro is used. It can also make code more readable, by employing a meaningful name instead of an unexplained number or operation.
- (2)
- At the desktop level, a program called by an application to run within a file or document. Applications that run macros have their own macro languages. For example, Microsoft Excel supports Excel Basic, a version of BASIC with Excel-specific tools. Macros can be attached to compatible documents, a useful feature that’s also the basis for a common form of malware. See also VBA.
- MAD
- Magnetic Anomaly Detection. A passive technology that finds metallic objects by looking for the local fluctuations that they cause in Earth’s magnetic field. The treasure-hunter’s metal detector generates its own magnetic field, so it’s more sensitive but has much shorter range.
- mag amp
- Magnetic Amplifier. A device that uses a saturated inductor as a switch for AC. It’s more robust than a vacuum tube, but both were eventually supplanted by transistors.
- AC normally experiences an inductor as an open circuit because the alternating magnetic field created by the alternating current through the inductor induces voltages that oppose that current. However, if the inductor core is saturated, meaning its magnetic field has reached the maximum strength the core will support, AC will pass through the inductor windings. In a mag amp, a second winding around the core carries a relatively small control DC that forces the core into saturation, or allows it to come out of saturation when the DC is removed.
- magnetron
- A device used in radar and microwave ovens to generate microwave radiation. It’s based on a cylindrical CRT with the cathode running along its axis, and the anode a thick-walled copper tube surrounding the cathode. A strong magnetic field parallel to the axis causes the cathode rays (free electrons) to travel in an arc rather than a straight line outward from heated cathode to anode. The anode has cylindrical resonant cavities running from end to end along its inner surface, and the arcing current flows around their circumference, inducing microwave radiation along them at a frequency determined by cavity size. Most microwave ovens operate at 2450 MHz, a frequency strongly absorbed by water molecules.
- makefile
- A collection of instructions for compiling a program. It lists source files, object files, and dependency information (e.g., if file A has changed, re-compile files B and C).
- Maksutov-Cassegrain
- See telescope.
- malware
- Malicious Software. Software that does bad stuff on purpose. In the good old days, malware was just vandalism, or even a prank, and spread chiefly by the sharing of floppy disks and CDs. Modern malware is designed to make money, gather information, exert control, or cause damage, by methods ranging from the unethical to the criminal. It usually spreads via the Internet (phishing, spam, QR code links, etc.). Infected USB thumb drives and CDs/DVDs are common too; they rely on MS Windows AutoRun or user actions to trigger their malicious versions of the
Autorun.infinstruction file. In rare cases, malware (or a vulnerability to it) is slipped into device firmware during manufacture. - Many users refer to any kind of malware as a virus, but that’s inaccurate. The section below covers the major classes, defined by both how they spread (macro virus, trojan, virus, worm) and what they do (adware, bot, keylogger, logic bomb, spyware). Real-life malware isn’t concerned with fitting neatly into a category, and is likely to exhibit the behaviors of more than one class.
- adware – Creates unwanted pop-up ads or links on a host computer, or redirects Internet searches. It’s rare for malware to do only this, so a PC that has adware probably has something worse too.
- bot – From “robot”. A program, benign or malicious, that performs automated tasks over a network. Although malicious bots (malbots) frequently spread themselves in the same fashion as worms, they can arrive as trojans, macro viruses, or traditional viruses too. Once a malbot has control of a network-connected device, it establishes a backchannel to one or more control sites on the Internet. These can be almost anything – IRC or HTTP servers, P2P sites, social-networking sites, etc.; some are set up intentionally as malware servers, while others have been hacked or just don’t monitor what they’re hosting. Bots check in frequently to pass information to and receive data, updates, and instructions from their controllers.
- A bot-controlled device is called a zombie. A group of zombies with the same controller is a botnet. Modern (2010) botnets can comprise hundreds of thousands of zombies, use encryption to protect themselves, and have long, constantly changing lists of control sites they can check in case some are compromised or shut down. In addition to stealing user data and using virus tricks to conceal themselves, botnets use their zombies as proxies to send spam; spread malware; host pornography or illegal activity; and launch DDoS attacks against security sites, rivals, spam/malware critics, or anybody the botnet controllers don’t like or are paid to attack.
- keylogger – A type of spyware that records what the user types on the keyboard, usually for the purpose of stealing account passwords, credit card numbers, etc. This is a common feature of worms and malicious bots. There are hardware keyloggers as well, but installing one requires physical access to the target system.
- logic bomb – Also called “slag code”. An old-school type of malware that destroys or corrupts stored data when activated. Since its purpose is targeted destruction rather than (like a virus) continual spread, it might have a time-delay trigger or be activated by specific system events – or the absence of specific events.
- macro virus – A sub-class of virus written in a macro language and attached to a document file that supports that language. Opening the document with an application that can run macros triggers the virus. Because MS Office applications are integrated with messaging apps, Office macro viruses can E-mail themselves to other users. In the early 2000s they were the world’s most common kind of virus. See VBA.
- spyware – Gathers data (passwords, keystrokes, credit card numbers, Internet search history) from the host PC and reports it, usually through a backchannel, to the spyware’s controller. Caveat emptor: some well-known corporations put spyware features into their software.
- trojan – From the legend of the Trojan horse. Apparent first use of the term for software was a 1974 Air Force paper on the security of the Multics OS, cited by Ken Thompson in his famous 1983 speech to the Association for Computing Machinery (ACM) about his backdoor hack of the C compiler. A trojan now means user-installed software, typically a freeware app or game, that secretly installs one of the other malware types.
- This is a long-established trick of online criminals. It’s also used by aggressive corporations to foist onto users the kind of unwanted software referred to collectively as crapware: free trial versions of software that loads itself into the start menu, or browser toolbars that show ads or direct traffic to the company’s sites. A corporation doing this sort of thing might mention it in the fine print of the end-user license agreement that you didn’t read, and might have an opt-out hidden in the installation process.
- virus – Hides and replicates itself within a computer file system by infecting files, i.e., modifying files to contain its executable code and to run it when opened. Besides the essential feature of self-replication, which uses up disk space and allows it to spread to other machines, a virus almost always carries an active payload. Early viruses would damage files, periodically display a message, or do something else obnoxious. Modern types install spyware and/or bot programs, creating a backchannel that makes the host PC available to the virus’s author for sending spam, launching DDoS attacks, hosting illegal activity, receiving commands and additional malware, etc.
- The more aggressive money-making viruses declare themselves to the user. So-called scareware types will, for example, claim to be anti-virus programs and urge the user to pay for emergency PC cleanup, masquerade as a government agency demanding payment of a fine or fee, or extort money by threatening to report the user’s alleged online crimes. The increasingly common ransomware types encrypt the user’s hard drive and demand payment to release it. Payment is typically extorted in a crypto-currency such as Bitcoin, both because it’s unconstrained by borders and because it’s difficult to trace. As of 2018, paying ransomware hackers results in recovery of the lost data only about half the time.
- A computer can be infected only if it executes software containing the virus. This is often the virus executable itself arriving as a download or an E-mail attachment, such as a .exe, .com, .vbs, .bat, or .shs file. The vector can also be a trojan, or a document file containing a macro virus.
- Increasingly, viruses copy themselves into essential system files and common executables, tamper with the system configuration (especially Windows Registry), disable anti-virus protections, block access to popular anti-virus sites, disguise their signature via polymorphism, write themselves into the BIOS, and use rootkit methods to hide, all of which makes them harder to detect and kill.
- worm – Propagates itself across networks, including wireless networks. Like a virus, it can be introduced by an executable or infected file that a careless user opens. Unlike a virus, it doesn’t have to start from an executable file stored on the affected system. A worm is a standalone program capable of infecting targets without human intervention. Once it has infected a server, it can attack any system that connects to the server, a trick called a drive-by download. It attempts to exploit programming flaws or vulnerable configurations of network-aware applications that a target is already running, or system backdoors left by other malware. The first worm released onto the Internet, on 2 November 1988, was an unsuccessful attempt by computer researcher Robert Morris, Jr. to create what would now be called a botnet.
- Systems on the Internet face a near-constant barrage of port scans from worms and bots that query random addresses for a response indicating an open TCP/IP port. If they get such a response, they follow up with an intrusion attack. One of the most common is the buffer overflow: pass a vulnerable application more data than it can accept, forcing it to write executable payload into the program-flow portion of memory. Another is the format string, in which a specially crafted query exploits an I/O function that has poor control of input types. Once in, worms cause the same sorts of trouble as viruses.
- Worms could exist purely in memory, in which case file-scanning anti-virus software (see IDS) wouldn’t catch them. However, turning off the system clears memory. To survive, worms burrow into the system in the same ways a virus does. Given this, and the ubiquity of network-capable applications in PCs, the line between bot, virus, and worm is blurry.
- New PCs connecting to the Internet for the first time are especially vulnerable to attack, like newly hatched sea-turtles scrambling toward the surf while seagulls swoop down to grab them. Even if a PC doesn’t visit malicious or compromised sites, malicious bots and worms searching at random for targets will be probing its defenses within seconds. Yes, seconds. The survival time (time until actual compromise occurs) of an Internet-connected PC with no firewall or security software can be as low as a few minutes, although it varies considerably with the current threat environment, the type of Internet connection, the OS, and other factors.
- To greatly reduce the danger to a new PC, before connecting it to the Internet, 1) give your user account a password that isn’t the kind of thing an idiot would have on his luggage (see dictionary attack) and that you don’t use for anything else; 2) make sure the OS firewall is on; 3) deactivate unnecessary network services, especially file- and print-sharing; and 4) connect the PC to the modem through a router that has its own firewall. First thing after connecting, go to the site of the OS vendor to download and apply updates and security patches. Do the same for the installed security software, if any.
- Continue to update OS and security information regularly for the life of the machine. Most such software has the capability to retrieve updates automatically. Never, never leave a PC connected with its firewall off.
- MAMR
- Microwave-Assisted Magnetic Recording. A hard disk drive data-storage technology, very similar to HAMR but using microwaves instead of laser light.
- MAN
- Metropolitan Area Network. Bigger than a LAN, smaller than a WAN.
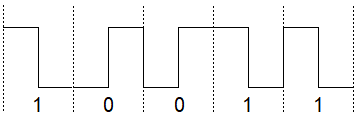
- Manchester coding
- Named for University of Manchester, UK. A digital coding technique that divides a binary signal’s period into halves, and uses a change in voltage level to differentiate the two halves. For this reason, the signaling frequency is twice the bit rate. A binary “1” is indicated by a high voltage in the first interval and a low voltage in the second interval. A binary “0” is the reverse case. The point is to prevent loss of synchronization that could occur with single-level source coding when the data contains a long string of ones or a long string of zeros. Compare NRZ, RZ.
- MANET
- Mobile Ad-hoc Network. A self-organizing, self-healing network with dynamic membership and no infrastructure or essential nodes. Obvious military potential. More demanding than a PAN.
- man page
- Manual Page. Dating to the beginning of Unix, this is a text file that contains the documentation for a command. In the command line interface for Unix or one of its descendants, enter
man commandto view the man page forcommand. - mantissa
- The fractional part of a logarithmic value, i.e., everything after the decimal point.
- MAP
- (1)
- Maximum A Posteriori. A type of soft-decision symbol decoder that minimizes BER.
- (2)
- Manifold Absolute Pressure. Refers to pressure in the air intake manifold of an internal combustion engine, or a sensor to measure it. Used to determine engine load. Compare BAP.
- MAPI
- Messaging API. See API.
- maser
- Microwave Amplification by Stimulated Emission of Radiation, originally. Same thing as a laser, but at lower frequencies, in the microwave range.
- MASINT
- Measurements and Signatures Intelligence.
- MATLAB
- From “MATrix LABoratory”. A widely used program from The MathWorks, Inc. for analyzing data, modeling systems, and performing other signal processing operations. Its command-line interface can import data from and export it to files, instruments, and some applications (e.g. Excel, Word), and can call tools created with other programming languages. It provides support for development platforms such as Arduino, Raspberry Pi, and LEGO’s NXT-G, and has many tools of its own for filtering and 2D or 3D display. Simulink, a popular MathWorks application that integrates with MATLAB, provides a graphical interface for model-based design.
- ASCII-format MATLAB script files, or M-files, are macros denoted by the .m extension, and contain a series of text commands.
- MAU
- Medium Access Unit. An IEEE term for a device, such as an Ethernet transceiver, that physically connects a processing node to a network. Sometimes incorrectly used for an MSAU.
- MAV
- Micro Air Vehicle. A very small flying machine, typically for carrying sensors. It’s a sub-category of UAV.
- MAX
- Measurement & Automation Explorer. A National Instruments interface for configuring, connecting, and controlling both hardware and LabVIEW virtual instruments (VIs).
- Maxwell’s demon
- Named for Scottish physicist James Clerk Maxwell (1831-1879). A hypothetical decision-making entity that, in a thought experiment, could sort molecules according to velocity, creating a thermal differential at no cost in violation of the Second Law of Thermodynamics. Information theory has established that there is a cost: each sorting operation requires the demon to use one bit of memory, expending a minimum [kB T ln(2)] joules of energy, where kB is Boltzmann’s constant and T is temperature.
- Maxwell’s equations
- Scottish physicist James Clerk Maxwell (1831-1879) developed the theories explaining the interdependence of electricity, magnetism, and EM fields. English scientist Oliver Heaviside (1850-1925) applied the new mathematics of vector calculus to codify Maxwell’s work as four elegant equations. There is more than one way of expressing them. In differential form, they are:
- Maxwell’s addition of the electric flux effect to Ampere’s Law, and his recognition that it and Faraday’s Law describe a constant interaction between electricity and magnetism, is what makes these relations so important.
- MBAN
- Medical Body Area Network. A network of body-worn sensors, with low-power RF links in the 2360-2400 MHz range. See also MedRadio.
- MBD
- Model-Based Development (or Design). A system-development approach that creates a platform-independent model of the end system, and uses it to generate one or more platform-specific models and interface definitions for them. These platform-specific models become the basis for creating requirements and proceeding to the development stage. However, unlike the similar MDD, there’s no automated code generation. UML is the usual modeling tool.
- MBR
- Master Boot Record. Also called master boot sector. Under the IBM drive-partitioning scheme for PCs, when a computer formats a hard disk drive or other data-storage device as a bootable drive, it makes the first drive sector the MBR, containing the disk’s master partition table and bootstrap loader (BSL). At startup, after the PC BIOS initializes system hardware, it loads the BSL from the MBR to a fixed address in main memory and runs it. The BSL directly or indirectly launches the operating system from the system partition identified by the master partition table.
- Malware commonly seeks to modify the MBR of any PC it infects. If it succeeds, it can not only make itself invisible to the OS and any security software, but can even protect itself from a reformat of the drive.
- MBSE
- Model-Based Systems Engineering. Systems engineering that uses methods and tools such as MBD and UML, as opposed to creating documents that describe the design and requirements.
- MCA
- Micro Channel Architecture. An obsolete IBM proprietary 16- or 32-bit expansion bus for the PS/2 series of PCs.
- MCC
- Memory Chip Controller. Also just memory controller. The PC component that links the memory bus from main memory to the CPU. Until the mid-2000s, it was always on the motherboard, bridging the CPU bus to the memory bus. Newer technologies put it on the CPU die.
- MC-CDMA
- Multi-carrier Code Division Multiple Access. A mix of CDMA and OFDM.
- MCH
- Memory Controller Hub. See MXT.
- MCM
- (1)
- Multi-Carrier Modulation. Transmitting data by dividing the bit stream into several parallel streams.
- (2)
- Multi-Chip Module. A circuit board with more than one IC chip on it and short, tightly packed connections. The term can also refer specifically to a type of mounting board for a Pentium chip. Newer high-density design approaches include SiP, SoC, and SoP.
- MCR
- Molded Carrier Ring. See JEDEC.
- MCU
- Microcontroller Unit. Same thing as a microcontroller.
- MCX
- See cable connector.
- MDA
- (1)
- Monochrome Display Adapter. See graphics.
- (2)
- Model-Driven Architecture. See MDD.
- MDD
- Model-Driven Development (or Design). Sometimes called model-driven architecture (MDA) or engineering (MDE), although it can be argued that MDA is just the initial stage of MDD, and MDE is a superset of both activities. MDD is the practice of using modeling software to create a simulation of a physical system from requirements, refine it with increasing levels of detail, and finally auto-generate the source code to implement it. The modeling software also provides the means to test and verify the design throughout development. The development flow conforms to what MDD calls a V-diagram, where the two branches – development and automated testing – converge on the final implementation.
- As compared to traditional software development, which goes from specifications to requirements to manual coding and then testing, followed by deployment and maintenance, MDD allows developers to catch errors earlier in the development cycle where it’s easier and cheaper to fix them. Contrast MBD.
- MDF
- Main Distribution Frame. See distribution frame.
- MDIP
- Molded Dual In-line Package. See JEDEC.
- MDM
- Mobile Device Management. Remotely managing the sofware on a computing device, especially a smartphone or notebook PC. Also, the installed software that provides this capability. Corporations routinely use MDM to maintain and update software on employee devices, and to restrict what employees can do with them. They sometimes do this to customer devices as well.
- MDP
- Mini DisplayPort. See DisplayPort.
- ME
- Management Engine. Since 2008, a low-power microprocessor in the chipset of Intel-based PCs that has admin-level access to hardware. It monitors system firmware during bootup and does various things related to security, including running network security software called AMT (Active Management Technology) and implementing playable media DRM. Details are Intel proprietary, but it is known to run the MINIX 3 operating system.
- MedRadio
- Medical Device Radiocommunications Service. In 2009, the FCC designated this RF band from 401 to 406 MHz for use by implanted medical devices, replacing the slightly narrower MICS band. Its use doesn’t require a license, although device EIRP must be within the low power constraints of the standard to be legal. In 2011, the FCC added four new bands – 413-419, 426-432, 438-444, and 451-457 MHz – specifically for devices that support function of limbs and organs.
- MEID
- Mobile Equipment Identifier. Like the older IMEI, a 56-bit ID number for mobile devices, but not constrained in the values it can use. Created in 2006 for CDMA systems. Also compare ESN.
- meme
- From the Greek mimeme (something imitated), pronounced “meem” to emphasize its conceptual similarity to “gene”. Its originator, biologist Richard Dawkins (1976), described it as a unit of cultural inheritance. On the Internet, it has come to mean something like a catch-phrase: A recurring cultural detail that evokes a distinct frame of reference for those who recognize it, e.g., “The cake is a lie,” or, “correct horse battery staple”. It can also be an image.
- A memecoin is a cryptocurrency that’s based on an Internet meme, or sometimes on a well-known person, and that relies on the popularity of that meme or person to create a perception of value. Memecoins suffer from even higher rates of fraud and volatility than other cryptocurrencies.
- memristor
- Memory Resistor. Sometimes called “memresistor”. First proposed in 1971 as a theoretical fourth fundamental element of circuits, in addition to RLC (resistor, inductor, capacitor): a resistor with memory. Its resistance changes with the amount and orientation of the voltage across it. When the write voltage is removed, the device retains the resistance, which can be non-destructively read with a much lower voltage. Unlike most binary logic devices, memristors are not restricted to two states.
- The first (2008) successful proof-of-concept used two layers of titanium dioxide – normally an insulator, but one layer had too few oxygen atoms, making it a conductor. Voltage caused O+ ions to migrate between the layers, changing the device’s overall resistance. Other approaches have since been found. However, many scientists don’t consider these variable-resistance devices to be equivalent to the theory. The memristor as originally conceived is now known to be impossible without inductance. If ever sorted out, memristors hold the promise of higher speed, greater density, and lower power consumption than transistor-based circuits.
- MEMS
- Micro-Electrical Mechanical System. An electromechanical device with tiny moving or hydraulic parts, most commonly made of silicon: gears, cantilevers, diaphragms, fluid channels. These devices have potential for satellites, since they’re intrinsically more radiation-resistant than conventional circuits. MEMS is also the basis for an optical switching technology that uses 1D, 2D, or 3D arrays of microscopic mirrors to redirect incoming beams from fiber-optic cables. Because switching is increasingly the bottleneck for the Internet’s fiber-optic backbones, this is a very hot field as of 2000.
- Rival MEMS technologies in research include refractive bubbles, liquid crystals, thermo-optics, holograms, liquid gratings, and acousto-optics. A promising power source is nuclear batteries, which generate power from the decay of radioactive materials, e.g. electrostatic force from beta particles (electrons).
- MEO
- Medium Earth Orbit. Not much used because this is the region occupied by the Van Allen radiation belts. MEO satellites are at 5000-12,000 km, an orbit that falls more or less between the belts. They orbit with low eccentricity, 30°-90° inclination, a period of 5-8 hours, and a speed of about 5 km/s. Signals passing through a MEO satellite incur at least a 110-130 ms round-trip delay.
- MeRAM
- Magnetoelectric Random Access Memory. A type of NVRAM (non-volatile RAM) that stores data as orientation of electron spin, and uses an applied field to change the spin.
- MESFET
- Metal-Semiconductor Field-Effect Transistor. See transistor.
- mesh network
- The older hub-and-spokes topology, used even by such recent standards as Wi-Fi (802.11), can be overloaded by large numbers of users or damaged by the loss of a router/access point. A mesh topology can use any member of the network as a relay, thanks to constantly updated routing tables. (This is essentially how the Internet works.) In this way, nodes that are out of range of one another can still communicate, their messages passing peer-to-peer without ever going through a control point. Wireless mesh networks do use Internet access points (IAPs), but, again, devices that are out of range can still access them.
- metadata
- Broadly, data about data, as opposed to the content of the data. File metadata is embedded information about where, when, how, and often by whom the file was created and modified. (See EXIF.) For document files, this can include original text that has supposedly been removed. Network metadata is about traffic: who made a connection, when, to where, what protocols were used, what kind and quantity of data was passed, etc.
- methane
- A gaseous alkane hydrocarbon, CH4, the principal component of natural gas. See LNG.
- methanol
- CH3OH, also called methyl alcohol or wood alcohol. A common fuel, including in fuel cells. It’s produced from the destructive distillation of cellulose, or, more often nowadays, from natural gas (methane). Besides being corrosive to aluminum, it’s a neurotoxin. A typical lethal dose is 80 to 150 mL. Compare ethanol, propanol.
- metric system
- See SI, or use the metric conversions page.
- metrology
- Broadly, the science of measurement. In manufacturing, it refers to tools and practices for verifying that products conform to the required tolerances. In semiconductor manufacturing, those tolerances can be in the nanometers.
- MF
- Medium Frequency. 300-3000 kHz. See RF.
- MFA
- Multi-Factor Authentication. A security standard that requires two or three independent factors to verify a user. The three factor types are something you know (e.g., a password), something you have (e.g., an ID card or a numeric key generator), and something you are (e.g., biometric data). Requiring just two of these is two-factor authentication (2FA).
- MFC
- Microsoft Foundation Classes. A hierarchical Microsoft library (e.g.
mfc42.dll, mfc70.dll, mfc70d.dll) of C++ classes for writing Windows applications. The first version came out in 1992. CObject is the root class of MFC, the ancestor of most of its base classes by way of its child CCmdTarget. CWnd is derived from CCmdTarget, and its many child classes include CFrameWnd, CDialog, CView, CPropertySheet, CButton, and CComboBox – every control is also a window. CWinApp is the Windows application class (derived from CWinThread, derived from CCmdTarget), so every MFC application is an instance of a class derived from CWinApp. Compare ATL, .NET, WTL. - MFD
- Multi-Function Device. For example, see MFP.
- MFLOPS
- Millions of Floating-point Operations Per Second. See FLOPS.
- MFP
- Multi-Function Printer. A printer that also serves as a scanner, photocopier, and fax machine.
- MFSK
- (1)
- Multiple (or M-ary, or Multi-level) Frequency Shift Keying. See FSK.
- (2)
- Minimum Frequency Shift Keying. A longer name for MSK that invites confusion with (1).
- MGA
- Monochrome Graphics Adapter. See graphics.
- MGC
- Manual Gain Control.
- MHTML
- MIME HyperText Markup Language. Little-used Microsoft “standard” Web page format introduced in 1999 to compete with HTML. MHTML files usually have the .mht extension.
- MHz
- Megahertz. 106 hertz.
- MiB
- Mibibyte. See byte.
- MIC
- (1)
- Microwave Integrated Circuit. See MMIC.
- (2)
- Media Interface Connector. See fiber.
- microcomputer
- Obsolete name for the class of microprocessor-controlled computers that includes the PC.
- microcontroller
- Also called a microcontroller unit (MCU). A single-chip computer with a narrow set of capabilities, and modest processing power compared to a microprocessor. As the name suggests, it typically monitors and controls external processes. It’s the basis for an embedded device, and includes a CPU, memory (RAM and/or ROM), I/O, and other peripherals as needed. There are many manufacturers of this sort of controller.
- Smartphones and other mobile devices with actual computing power depend on a more capable breed of microcontroller, really a low-end microprocessor, often dubbed a system on a chip (SoC). See ARM, Intel.
- micro-DIMM
- A standard for DRAM circuit cards, smaller than the mini-DIMM. Manufacturers can use different heights than those given below.
- The 144-contact version, used for PC133 SDRAM, measures 1.545" × 1".
- The 172-contact version for DDR or DDR2 SDRAM is 1.67" × 1.18", with different latch-hole arrangements for DDR and DDR2.
- The 214-contact version for DDR2 SDRAM is 54mm × 30mm with a mezzanine connection rather than an upright card-to-slot interface, so it installs parallel to the motherboard. The heights can vary.
- microprocessor
- A more general-purpose and powerful device than the microcontroller, this chip is the brain of almost all computers. It controls the interpretation and execution of instructions. In modern usage, “microprocessor” and “CPU” usually mean the same thing, but this wasn’t always so. In older computers, the components of the CPU were physically separate. The microprocessor put it all on one chip. Compare GPU, APU.
- The desktop microprocessor market since the late 1990s has been dominated by just two companies, Intel and AMD. IBM, Motorola, Cyrix, NexGen, Zilog, and IDT have also made microprocessors for desktop systems.
- microwave band
- The higher-frequency part of the RF spectrum. The military divided it into bands during WWII. At the time, it was used only for radar, and the arbitrary, confusing band designations were a security measure. The FCC, NTIA (National Telecommunications and Information Administration), and NRAO (National Radio Astronomy Organization) are pushing for the abandonment of these designations, with little success.
- The microwave bands are now used for satellite and terrestrial communications as well. Different users divide these bands into sub-bands, and often disagree about where they start and stop. Below are the standard IEEE definitions.
- There are other bands that are not universally recognized:
- Microwire
- See SPI.
- MICS
- Medical Implant Communications System. In 1999, the FCC designated this RF band from 402 to 405 MHz for use by implanted medical devices, which necessarily have low power and short transmission range. It was subsumed by MedRadio in 2009.
- MID
- Mobile Internet Device.
- MIDI
- Musical Instrument Digital Interface. A fairly demanding standard for synthesizing instrumental sounds. It has 128 notes, numbered 0 to 127. Base level synthesizers can play six notes on three melodic instruments and three notes on three percussion instruments simultaneously. Extended-level synthesizers can do 16 notes on both nine melodic and eight percussion instruments at once. General MIDI synthesizers can handle 24 voices, or 16 notes on 15 melodic channels plus 8 notes of percussion. Instrumental files can be MIDI-mapped to the synthesizer to set their volume and key. MIDI files (.mid extension) are smaller than MP3 files and vastly smaller than WAV files, but the sound varies with the system playing it. MIDI connectors are typically 5-pin DIN.
- Mie scattering
- Named for German physicist Gustav Mie (1869-1957). A mechanism that causes light to be scattered by particles with little regard to wavelength – e.g., the bright white region of sky around the Sun. Rayleigh scattering is a more pronounced phenomenon, so Mie scattering is noticeable only for wavelengths where Rayleigh scattering is weak.
- MII
- Media Independent Interface. A 40-pin mini-D connector for linking a Fast Ethernet physical device (PHY) – a hub, switch, or router – to a device that uses the Media Access Control (MAC) protocol. Put another way, it connects an OSI layer 1 to an OSI layer 2 device. Variants include the RMII (Reduced MII, 7-pin), SMII (Serial MII, reduced pinout), and SSMII (Source-Synchronous MII). For the later, faster versions of the Ethernet standard, there’s the backward-compatible GMII (Gigabit MII) and XGMII (10-Gigabit MII, “X” being the Roman numeral 10). The 72-pin XGMII has 32 transmit lines, 32 receive lines, and 4 flow-control lines each for Tx and Rx.
- mil
- One-thousandth of an inch (0.001").
- mile
- From “mille”, Latin for 1000, referring to the distance a Roman legion could march in 1000 paces (a pace being two steps). The US statute mile is 5280 feet, or 1609.344 meters. The old British or Admiralty nautical mile was 1853.18 m. In 1929, the international nautical mile was set at 1852 meters, roughly equal to 1 minute of latitude, and the US nautical mile was changed to match in 1954. There’s more, but why not just use SI?
- MIL-STD-1553
- Military Standard 1553. A data bus standard created for use aboard aircraft, spacecraft, and missiles, specifying both the physical layer and the communications protocol. It connects a single bus controller (BC) with up to 31 remote terminals (RTs), or 32 under the original MIL-STD-1553A specification from 1975. The bus has two separate channels, A and B, each of which is a differential pair. The redundant channel B is used as a fallback if there’s no response on channel A. Data is sent at 1 Mb/s, but since the standard uses Manchester coding, the signaling rate is actually 2 MHz.
- The BC is the only device that can initiate a message. It issues commands to the RTs to prepare to receive, and to send. RTs can send to other RTs only when commanded to. A RT that’s configured as a bus monitor (BM) cannot send.
- A MIL-STD-1553 bus message is one or more 20-bit words, each consisting of 3 sync bits (actually a line high and line low each occupying 1.5 bit periods), 16 data bits, and a final parity bit implementing odd parity. The first word of any message from the BC is a command, with the structure shown below.
- The RT with configured address matching bits 4-8 of the command word accepts the message, while all other RTs ignore it. (In the MIL-STD-1553B specification, RT address 31 is reserved for broadcast. Any RTs configured to receive broadcasts accept command messages addressed to RT 31, but don’t reply to them.) For normal data transfers, the Tx/Rx bit of the command word tells the RT whether it’s being commanded to send data (1) or receive data (0), and word count is how many data words are being sent or received, from 1 to 32. A word count of 00000 means 32, not 0. The 5-bit subaddress (SA) specifies any of up to 30 different message types for the RT. A subaddress of 0 or 31 tells the RT to treat the word count as a mode code, with a meaning defined by the standard. Command messages with mode codes 17, 20, and 21 each have one following data word, as do response messages to mode codes 16, 18, and 19.
- It’s common practice to represent command words in an abbreviated hexadecimal format. For example, 0C R 05 14: 0C means RT address 0x0C (decimal 12), R (or 0) means prepare to receive, 05 means subaddress 0x05 (5), and 14 means word count 0x14 (20). The core 16 bits of that same command word are binary 0110000010110100, or hex 0x60B4.
- The RT replies to a non-broadcast command message with a status word reporting RT status and whether the command was received correctly. Bits 4-8 of the status word are the address of the responding RT, and bits 9-19 are one-bit status codes that, if set, have the meanings shown below.
- If the command was to send, the response message follows the status word with however many data words were commanded, between 1 and 32. If the destination of a data response is another RT, that RT will respond with a status word of its own – for the benefit of the BC, not the first RT.
- MIMD
- Multiple Instructions Multiple Data. A multi-core or multi-processor technique for parallel processing, with each running independently, executing a different process or a different thread of a shared process. Compare SIMD.
- MIME
- Multipurpose Internet Mail Extensions. Internet classification system, also called content types or media types, for identifying file type (HTML- or XML-based Web page, image, etc.) to servers and browsers. Originally a supplement for the 7-bit ASCII of SMTP, enabling e-mail and, later, Web pages to use extended ASCII or non-English characters, text formatting, images, sound, video, executables, etc.
- MIMO
- Multiple Input, Multiple Output. An RF link that uses a phased array of multiple antennas at both the transmitter and the receiver, backed by advanced DSP, to overcome difficult RF environments, improving signal gain without using more power. It’s common in wireless networks of all kinds, e.g., 802.11n and LTE Advanced. It will be more common in future communications systems – especially those employing higher frequencies that are currently unallocated because of high atmospheric attenuation. Compare MISO, SIMO, SISO.
- MIN
- Mobile Identification Number. An ID number that a wireless provider assigns to each subscriber device, separate from the ESN and other identifiers. Usually, it’s just the phone number.
- minicomputer
- Obsolete class of what would now be called a server: a mid-range, multi-user computer with the architecture of a mainframe, and more power than a single-user workstation or microcomputer (which would now be called a PC). Includes DEC’s groundbreaking PDP-# series.
- mini-DIMM
- A smaller, 244-contact version of the DIMM, used for DDR or DDR2 SDRAM (see DRAM). It measures 82mm × 18.28mm (VLP, very low profile), with a notch dividing its contacts into groups of 114 and 130. There are unbuffered ECC Mini-UDIMM and registered Mini-RDIMM versions for special applications.
- References to a 200-pin mini-DIMM are probably confusion with the 200-pin SO-DIMM.
- mini-UHF
- See cable connector.
- MIPS
- Millions of Instructions Per Second.
- MISO
- (1)
- Multiple Input, Single Output. An RF link that uses one receiving antenna, typically supported by path-analyzing DSP, to reconstruct a signal from a transmitter that uses multiple antennas. Compare MIMO, SIMO, SISO.
- (2)
- Master Input/Slave Output. See SPI.
- MISRA
- Motor Industry Software Reliability Association. A UK industry group, at https://www.misra.org.uk. In 1998, they released MISRA C, a set of 127 rules for writing ANSI/ISO C code so as to reduce the risk of errors and increase readability. Embedded device programmers often follow these rules.
- MitM
- Man in the Middle. A network attack in which a third party intercepts data and/or reroutes connections by secretly acting as a relay between two nodes. To each node, communications sent by the MitM appear to be from the other.
- ML
- Machine Learning. A form of AI.
- MLC
- Multi-Level Cell. See flash memory.
- MLCC
- Multi-Layer Ceramic Capacitor. The most common form factor for ceramic capacitors: an IC chip containing hundreds of metal capacitors connected in parallel and separated by thin layers of a ceramic dielectric.
- MLP
- Micro-Leadframe Package. See JEDEC.
- MM
- (1)
- Multi-Mode. A type of optical fiber with a large (50 or 62.5 µm) central core. The core-cladding interface perfectly reflects signals so that light will refract through the cable. It’s cheaper than single-mode (SM) because the electronics at the ends don’t need the same degree of precision, and a LED rather than a laser will suffice as the light source. Transmission distance is limited to about 2000 m.
- (2)
- Machine Model. See ESD.
- MMC
- Multi-Media Card. A small JEDEC-standard data card using flash memory. It measures 24 × 32 × 1.4 mm, or 24 × 18 × 1.4 mm for the reduced-size RS-MMC (some other form factors exist), and offers capacities up to 4 GB. Largely supplanted by the similar and usually compatible SD card.
- MMCX
- See cable connector.
- MMDS
- Multi-channel, Multi-point Distribution Service. A type of LOS broadband wireless interface system that transmits at 2.5 GHz, with a coverage radius in the tens of kilometers.
- MMF
- Multi-Mode Fiber. See MM.
- MMI
- Man-Machine Interface. A broad term for anything that allows a person to interact with a machine. A GUI is one obvious example; a BCI is less obvious.
- MMIC
- Monolithic Microwave Integrated Circuit. A microwave IC (MIC) produced by simultaneously forming components, such as semiconductor devices, passive circuit devices, and transmission lines, on a semiconductor substrate – often GaAs rather than silicon.
- MMJ
- Modified Modular Jack. A 6-pin connector, similar to those used for the USOC RJ## standards, but with the locking tab off-center. It’s a DEC proprietary design to connect serial terminal lines with terminal devices.
- MMO
- Massively Multi-player Online. A class of computer game in which many players interact in a common Internet environment.
- MMS
- Multimedia Messaging Service. A standard for using mobile phones from 3G or GPRS-enhanced 2G onward to transmit messages larger than the 140- or 160-character limit of SMS, including embedded multimedia content – images, video, and audio as well as text. The sending device encodes and uploads the message. The wireless provider’s Multimedia Messaging Service Center (MMSC) extracts the content, converts it to HTTP, and sends a link to the receiving device, which uses WAP to access it. Alternately, if the MMSC determines that the recipient’s device is not MMS-capable, it transfers the content to a Web host and sends a link to the URL.
- The standard doesn’t set a maximum message size, but providers commonly cap it at 300 or 600 kB.
- MMU
- Memory Management Unit. A hardware component that manages CPU access to memory. One of its most important jobs is optimizing use of high-speed memory caches, to minimize use of the much slower main memory.
- MMX
- Multi-Media Extension (for trademark purposes, Intel denies that MMX is an acronym). Intel’s 1996 set of 57 multimedia instructions for use by x86 chips, cross-licensed with AMD, cutting out Cyrix. The idea is that, while the processor is 32-bit or 64-bit, the video and audio data come mainly in packets of 8 to 16 bits. MMX supports single-instruction, multiple-data (SIMD) operations, meaning the same operation performed on several data values at once.
- MNP
- Microcom Networking Protocol. A series of proprietary Microcom, Inc. protocols for modems operating over analog phone lines, common from the 1970s into the 1990s. MNP 2 through MNP 4 are error correction protocols. MNP 5 is a data compression protocol. The V.42 error correction protocol uses MNP 4 as its backup scheme (its primary being LAP-M). The V.42bis data compression protocol doesn’t use MNP 5, although V.42bis modems have both. MNP 6 through 10 were little used.
- MOA
- Minute Of Arc. One sixtieth of a degree of angular rotation.
- mobo
- An abbreviation of motherboard.
- MOCVD
- Metal-Organic Chemical Vapor Deposition. See CVD.
- modem
- Modulator/Demodulator. A device that converts a computer’s digital data into a signal for transmission over some medium, and converts signals received via that medium into digital data.
- Voice-band modem standards, such as the V.## series from the ITU (formerly CCITT), define modulation and protocols for exploiting the voice-grade channel passband of a telephone line, between approximately 300 and 3400 Hz. The V.## series are analog modems, requiring a normal analog connection to the telephone company’s local loop. They might have line problems caused by trunk components and switches that limit bandwidth to reduce line static, narrowed channels on interoffice phone systems, and telco digital speech compression of analog circuits.
- Digital modems, such as broadband cable and DSL modems, connect to the public switched telephone network (PSTN) through a link to a server run by the cable TV company or telephone company. The old narrowband types with claimed 56 kb/s speeds generate digital samples for use by the PSTN. Phone line power limits and D/A conversion issues at the switching office prevent them from reaching 64 kb/s, the actual phone channel bit rate.
- modular connector
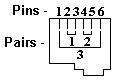
- Any of the multi-contact plugs or jacks defined by the ISO as 4P2C, 4P4C, 6P2C, 6P4C, 6P6C, 8P2C, 8P4C, 8P6C, 8P8C, 10P2C, 10P4C, 10P6C, 10P8C, and 10P10C. P is number of positions, meaning how many electrical contacts the plug or jack can have, and C (connections) is how many it actually does have. The USOC registered jack (RJ##) telephone wiring standards employ many of these connectors. Ethernet (IEEE-802.3) uses 8P8C connectors, commonly but inaccurately called RJ45.
- modulo 2
- A binary arithmetic operation denoted by the ⊕ symbol, and equivalent to the exclusive-OR of binary logic: add binary numbers with no carry. For example, 10110 ⊕ 00111 = 10001.
- mole
- Also mol, from “molecule”. 6.0221367 × 1023 atoms or molecules of any pure substance. This value, also called Avogadro’s number (NA) or Avogadro’s constant, is a SI standard, defined as the number of atoms in 12g of carbon-12. An element’s atomic number is the mass (in grams) of 1 mole of that element.
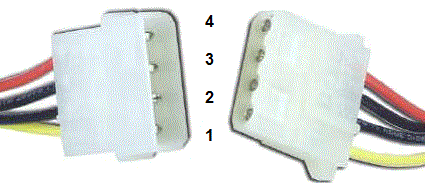
- Molex
- A major manufacturer of electrical connectors used in PCs. “Molex connector” commonly means the Molex 8981 series four-pin plastic header, the standard power connector for ATA disk drives; pin 1 is +12V, pin 4 is +5V, and pins 2 and 3 are ground. PC power supplies use other Molex connectors for fans, peripherals, motherboard main power (the ATX connector), etc.
- Molniya
- Russian молния, meaning “lightning”. A highly inclined (63.4°), highly elliptical (0.7 eccentricity) satellite orbit with a 12-hour period, giving it a roughly 8-hour dwell time high over the northern hemisphere. It’s used mostly by Russian comm satellites. Apogee is about 40,000 km (beyond GEO), while perigee is around 1000 km. The inclination keeps the satellites away from the worst of the inner Van Allen belt, which is thicker near the equator.
- moniker
- A COM object that is created and initialized by a client to perform a single instance of COM object creation and initialization for the client. Confusing? Yeah. The idea is that the task of creating and initializing the moniker object is relatively simple, while creating the ultimate target COM object might be very complex for the client.
- monolithic
- From ancient Greek μονόλιθος, meaning made from a single stone. An IC, including passive devices, on one semiconductor substrate.
- MOOC
- Massive Open Online Course. An online educational course that uses automation to serve a very large number of students.
- Morse code
- Named for American inventor Samuel F. B. Morse (1791-1872), who co-developed the first version for his telegraph. A quasi-binary code for transmitting alphanumeric data via any two-state medium as a series of dots and dashes. A dot means the medium is active for one time unit (of arbitrary duration), and a dash is when it’s active for three time units. There’s one time unit of inactivity between active states within a character, three units of inactivity after the end of a character, and seven after the end of a word.
- Since the first Morse code was for American English, other nations developed their own versions. The International Morse Code (circa 1865) eventually replaced many of them:
- Mosaic
- An early browser for the WWW and other Internet functions, descended from XMosaic and developed at NCSA.
- MOSFET
- Metal-Oxide-Semiconductor Field-Effect Transistor. See transistor.
- MOSI
- Master Output/Slave Input. See SPI.
- motherboard
- The large circuit board that provides the foundation for almost all personal computers. At a bare minimum, it hosts the CPU, memory, and interfaces for disk drives or other types of storage, and has expansion slots (mainly PCIe as of 2013 – earlier motherboards used ISA, EISA, VLBus, PCI, AGP, et al) for installing circuit cards that provide additional functions. Modern motherboards routinely have integrated network, I/O, sound, and modem capability, among other features. See northbridge, southbridge.
- Motif
- The Open Software Foundation’s tool package that runs on top of X Window. It includes mwm (the Motif window manager), which defines how windows behave.
- motor
- A device that converts electricity into motion (as opposed to an engine, which generates the power that it uses). Motors can be built to use either alternating current or direct current. Electric vehicles are powered by batteries, which are inherently DC devices, but have DC-AC inverters so that they can use the more efficient, versatile, and reliable AC motors.
- A DC motor passes current through a wire loop in the rotor, or armature, creating electromotive force between the electrified loop and the magnetic field of permanent magnets (or, for larger motors, electromagnets) in the stator. Since the rotor has to rotate, current must be supplied to it through stationary wire brushes in contact with rotating commutators. Multiple coils with split-ring commutators are typically used to smooth the speed of rotation.
- There are two broad types of AC motor:
- The induction motor is a mirror image of the inductive generator in that it, too, has a stator and a rotor, but uses electric current to generate motion rather than the other way around. AC in the stator windings creates a rotating magnetic field (RMF) that induces current in closed-loop conducting elements within the rotor. The induced currents in turn create magnetic fields opposing the RMF, and repulsion between these fields turns the rotor. This design, invented by Nikola Tesla, is also called an asynchronous motor because the speed at which it drives the rotor, while varying, is always less than that of the RMF. If external forces drive the rotor faster than the RMF, the motor can function as a generator.
- The synchronous motor is called that because the rotor rotates at the same speed as the stator’s RMF. Its performance is superior to that of induction motors. The most common approach, which dominates in electric vehicles as of 2024, uses permanent magnets rather than electromagnets in the rotor. Other synchronous designs rely on switched magnetic reluctance.
- Traditionally, the stator is an iron core wound with copper wire, but there are lightweight motor designs that use other materials. There’s also the electrostatic motor, a design that goes back to Benjamin Franklin and uses the attraction and repulsion between electric charges to generate motion. It uses much higher voltages but lower currents than an inductive motor, and so far is more efficient only at very small sizes.
- Motorola
- Major American communications equipment manufacturer. In 2024, they’re best known as a major manufacturer of Android smartphones. In the 1980s and early 1990s, Motorola produced the 68k (or 680x0) series, the four generations of 16- and 32-bit microprocessors used in Macintosh PCs: 68000, 68020, 68040, and 68060. There were variants of each. Later, Motorola collaborated with IBM on the PowerPC family of microprocessors.
- MOV
- Metal Oxide Varistor. A varistor based on semiconductor material that becomes less resistive with increasing voltage, shunting overvoltages to ground.
- MP3
- MPEG-1 Layer 3. The lossy audio compression format used by the MPEG-1 standard, with sampling frequencies of 32, 44.1, and 48 kHz. Although technically superior formats such as AAC have since been introduced, MP3 remains a popular online music file format. Files use the .mp3 extension.
- MP4
- MPEG-4 Part 14. Multimedia (sound & video) file format. Files normally have the .mp4 filename extension, or .m4a for audio-only. Unlike MP3, MP4 can support both lossless (e.g. ALAC) and lossy (e.g. AAC) compression schemes.
- MPA
- Microsoft Product Activation. Any of the anti-copying features Microsoft started building into its products in 2001. These include Windows XP’s Windows Product Activation (WPA); Office XP’s Office Activation Wizard (OAW); Windows Genuine Advantage (WGA), which was added to Windows XP in 2005 and built into Windows Vista and Windows 7; and Windows Activation Technologies (WAT), which is WGA with better manners and without the insultingly dishonest name.
- At installation, the software uses its own product key and a hash value derived from system hardware to generate an installation ID code. Upon receipt of this code – automatically via an Internet connection, or indirectly by phone – Microsoft supplies a confirmation ID. Without this ID, the software is non-activated. In Windows XP, an RC4-encrypted database file called WPA.DBL monitors activation state and hardware configuration. Non-activated Windows XP will run for only 30 days, and non-activated Office XP for just 50 uses. Non-activated Windows Vista or Windows 7 will at a minimum disable some features, including most updates.
- The various incarnations of MPA have been criticized for functioning as spyware (sending user information far in excess of what Microsoft needs to verify the license), and for deactivating valid installations because of hardware changes, service pack installation glitches, etc.
- MPEG
- Moving Picture Experts Group. A group within the ISO, established in 1988 to create standards for compressed video & audio signals. The term also refers to the files themselves, which have a .mpg or .mpeg extension. There have been three standards: MPEG-1, MPEG-2, and MPEG-4. Most PCs now support MPEG-1. MPEG-2 is the standard for DVD players. It requires higher bit rates than MPEG-1 to achieve its superior resolution. It can support broadcast-quality video within about 4 Mb/s, as opposed to 140 Mb/s for PCM-coded video. MPEG-4, also called H.264, was designed for broadcast. It supports interactive and 3D content and is being incorporated into 3G cellular terminals. See MP3, MP4.
- MPLS
- Multi-Protocol Label Switching. IP is connectionless by design. MPLS is an IETF creation that adds connection-oriented forwarding to IP. It identifies a path through the IP network, and assigns a label specifying that path to each of the packets in a session. The packets are routed through the network according to these labels, following what’s called a label-switched path (LSP). This allows quality of service and traffic engineering to be applied on the network.
- MPO
- Multi-fiber Push-on/Pull-off. See fiber.
- MPP
- Massively Parallel Processing. A computing method that has hundreds or thousands of closely coupled, scalar microprocessors working in tandem, with a separate OS running each.
- MPPP
- Multi-link Point-to-Point Protocol. Up to six 64 kb/s ISDN B-channels aggregated together.
- MPR II
- From “Mat och ProvRad”. A Swedish standard for ELF and VLF emissions from video monitors at a distance of 50cm. Supplanted by the stricter TCO.
- MPRAM
- Multi-Port Random Access Memory. A type of RAM, used on multi-processor boards, that has two or more I/O ports to allow access by two or more processors.
- MPSK
- (1)
- Multiple (or M-ary, or Multi-level) Phase Shift Keying. See PSK.
- (2)
- Minimum Phase Shift Keying. A longer name for MSK that invites confusion with (1).
- MPU
- Microprocessor Unit. See microprocessor.
- MQTT
- Message Queue Telemetry Transport, originally. An open-standard, low-power protocol for exchanging data between IoT devices using TCP/IP port 1883, or port 8883 if applying TLS encryption. It has a client-server architecture with one or more servers, known as message brokers. Client devices forward whatever messages they’re designed to send to a message broker, which passes them on to any clients that have subscribed to receive the type of message in question. (This is called publish-subscribe messaging.) The “queue” in the original name is a legacy of the protocol’s beginnings at IBM; it doesn’t use data queueing.
- MRAM
- Magneto-resistive Random Access Memory. A type of NVRAM (non-volatile RAM) that exploits the GMR or TMR effect. Each bit of data is held in a memory cell consisting of two ferromagnetic channels separated by a non-magnetic barrier so thin that electrons, exhibiting their wave nature, can tunnel across it. One of these channels has a fixed magnetic field, while the other, the free channel, can change its field orientation. If the magnetic fields have opposing orientation, resistance to the tunneling current is far higher than when the fields are aligned. MRAM reads this resistance as the boolean state of the cell, 0 or 1. Unlike DRAM or FRAM, MRAM reads state non-destructively.
- The original MRAM uses current in a data-write line to induce a magnetic field that sets the orientation of the free channel. This requires unacceptably high write power. Spin transfer torque (STT) MRAM achieves much lower write power by instead applying a spin-polarized current – that is, a current consisting of electrons whose spin is the opposite of the free channel’s current spin state, changing that state and thereby reversing the magnetic field.
- Though predicted to be the universal memory that will replace hard drives, PC main memory, flash memory, etc., MRAM is still fighting cost and memory-density issues as of 2014.
- MRI
- Magnetic Resonance Imaging. A medical imaging technology based on nuclear magnetic resonance (NMR). It applies a powerful magnetic field to align hydrogen atoms in the subject as dictated by their spin, and a RF signal to perturb this alignment. As the atoms re-align, they produce their own RF signal that yields an image through a slice of the subject. Unlike a CT scan, an MRI system can take this image through any desired plane. A series of images builds up a 3D picture. Compare PET.
- MSA
- Multi-Source Agreement. This means, variously, an agreement between multiple companies to develop a technology standard, the working group that produces the standard, or even the actual standard. It’s often used in this last sense to refer to SFF- and SFP-compliant devices.
- mSATA
- Mini-Serial Advanced Technology Attachment. See SATA.
- MSAU
- Multi-Station Access Unit. A node that connects one or more systems to a token ring network. Multiple MSAUs connect to form the ring. Physically closing the ring isn’t essential, but improves network reliability.
- MSB
- Most Significant Byte. The highest-valued byte in a multi-byte expression. For example, the decimal number 396,584,882 becomes 0x17A367B2 in hexadecimal form, so its MSB is 0x17. The most significant bit within a byte can also be denoted MSB, or MSb. Contrast LSB. See also endian.
- MSCDEX
- Microsoft Compact Disc Extension. A driver that allows DOS and Windows 3.x to recognize and control CD-ROM players. The driver is located in a file called mscdex.exe. Windows 95 replaces MSCDEX with a 32-bit, dynamically loadable driver called CDFS.
- MS-DOS
- Microsoft Disk Operating System. See DOS.
- MSDS
- Material Safety Data Sheet.
- MSGP4
- Merged Simplified General Perturbations. The combination of SGP4 and SDP4. See SGP.
- MSI
- Medium Scale Integration. A dated way of describing the density of an integrated circuit (IC). Once the first IC designs came to be considered small-scale integration, chips with 60 to 300 elements were dubbed MSI. See also LSI and VLSI.
- MSK
- Minimum Shift Keying. A type of CPM. It’s a special case of continuous-phase FSK (CPFSK) with a modulation index of 0.5. That is, the data rate is twice the excursion, which gives its spectrum a rounded top. The carrier phase of an MSK signal is advanced or retarded 90° over the course of each bit period to indicate a 1 or a 0. The modulator does this by multiplying the +1 and –1 of each NRZ bit stream (the I and the Q) by a sine wave with a 2-bit period, so each +1 or –1 is replaced with a half-wave sine function. Then it beats this data wave with the carrier wave, and adds the I and Q rails. The resulting MSK signal has two frequencies like FSK, and no phase discontinuities, greatly reducing undesirable side lobes.
- MSK can be regarded (and demodulated) as either 2-FSK or BPSK, but don’t call it MFSK or MPSK. Demodulation as FSK gives up 3 dB of signal strength, but has the virtue of being simpler. See constant envelope.
- MSOP
- Molded Small Outline Package. See JEDEC.
- MSP
- Management Service Provider. A type of company that maintains and manages network and Internet applications for corporate customers. A sub-type of ASP.
- MSPS
- Million Samples (or Megasamples) Per Second. See SPS.
- MSR
- Molten Salt Reactor. See reactor.
- MST
- Multi-Standard Terminal. A radio terminal that can operate on a number of different air interface standards. See SDR.
- MT
- See fiber.
- MTA
- Mail Transfer Agent. A client-server program to deliver e-mail using SMTP. If the intended recipient is local, the MTA holds it for user retrieval; if not, it forwards it to another MTA server.
- MTBE
- Methyl Tertiary-Butyl Ether. A gasoline oxygenate, (CH3)3COCH3, that pollutes groundwater.
- MTBF
- Mean Time Between Failures. A standard measure of reliability, given in hours.
- MTP
- See fiber.
- MT-RJ
- See fiber.
- MT/s
- Mega-Transfers per second. See T/s.
- MTSO
- Mobile Telephone Switching Office. The electronic middleman between cell towers and the PSTN.
- MTU
- Maximum Transmission Unit.
- MU
- See fiber.
- mu law
- See companding.
- multicasting
- A networking technique in which a single data stream is sent to multiple hosts using a new type of address, a host group address. This is as opposed to unicasting, where the originator must send a separate data stream to each intended recipient. IPv4 supports multicasting via the Internet Group Management Protocol (IGMP).
- multi-homed
- Having two or more hardware connections to a network, and a separate address for each.
- multi-mode
- See MM.
- multipath
- Also called Rayleigh fading. A RF effect wherein a transmission arrives at a receiving antenna by more than one propagation path, with slight time delays between the paths. This can cause serious interference problems. Modern DSP and digital modulation technologies can not only correct multipath interference, but in some cases exploit it to increase gain. See 802.11n, phased array, MIMO, MISO.
- multi-processing
- Using more than one processor core in a computer system, and sharing tasks between them. Sometimes called parallel processing.
- multi-tasking
- Running more than one application simultaneously on a computer system, as opposed to single-tasking, which is all the command-line operating systems of early PCs could do. Modern operating systems employ pre-emptive multi-tasking, meaning they force programs to share processor time and other system resources. Unix had this feature from the beginning, as did Commodore’s Amiga OS. Early versions of Windows and the Mac OS instead used co-operative multi-tasking, in which each application was written to cede time to others. This meant that one badly written program could make problems for all of them.
- multi-threading
- Dividing a running software program into two or more streams of execution, called threads, and interleaving them on the processor so that they run concurrently – not, technically speaking, simultaneously, since even the most advanced processor core is executing only one process at any given instant. The OS manages multi-threading, but requires a processor that supports it and software that’s written to be threaded. See also SMT.
- Besides supporting more complex software that can coordinate multiple activities in parallel, multi-threading can create faster, more efficient software. That’s because it’s common for programs or processes (a program can consist of more than one process) to contain long-latency operations that must wait for some input or external event, or that take a set amount of time. If the process runs as a single thread, other, faster operations have to wait until the slow one finishes even if they’re not dependent on it. A multi-threading system can recognize long-latency actions, split them off into their own thread, and run them concurrently with the faster actions so that the process as a whole finishes much sooner.
- This is similar to but distinct from multi-tasking, a much older (1960s) concept that uses time-sharing to support multiple programs on one processor. It’s also not multi-processing or parallel processing, which use more than one physical core to run processes.
- MU-MIMO
- Multi-User, Multiple-Input Multiple-Output. A version of MIMO that supports multiple users by splitting its available bandwidth into two or more equal-priority queues.
- mutex
- Mutual Exclusion. In programming, this refers to both tools and practices to prevent execution threads from modifying a shared data resource that other threads are currently using.
- mux
- Multiplex. Multiplexing means putting multiple signals on a single carrier, whether wired (electrical), wireless (RF), or optical (fiber).
- MVC
- Model-View-Controller. The division of software architecture into three sections, plus a user, with all of the interactions between them falling into just a few categories. First defined in 1979, it’s meant as a high-level model for software design.
- MVS
- Multiple Virtual Storage. A family of IBM mainframe operating systems dating to 1974.
- MW
- Microwave. See microwave band, magnetron.
- MWIR
- Mid-Wave Infra-Red. See IR.
- MX2
- The chemical formula for any of the transition-metal chalcogenides, which are semiconductors for making 2D transistors. The M represents one of a number of transition metals, and the X is one of the three chalcogenides: sulfur (S), selenium (Se), and tellurium (Te).
- MXT
- Memory Expansion Technology. Hot IBM technology (2001) for roughly doubling available memory using compression algorithms. The memory controller hub (MCH), which resides between the processor and RAM, implements MXT and uses its own Level 3 cache to support the compression/decompression algorithm.
| ∇ • D = ρV | Gauss’s Law of electric fields: Total electric flux D through the surface of a volume V equals total electric charge within that volume |
| ∇ • B = 0 | Gauss’s Law of magnetic fields: Total magnetic flux B through the surface of any volume is zero (i.e., there is no magnetic charge or magnetic monopole; half a magnet remains a magnet) |
| ∇ × E = -δB/δt | Faraday’s Law: A time-changing magnetic flux B through a circuit induces an electric field E within that circuit |
| ∇ × H = δD/δt + J | Ampere’s Law: An electric current J generates a magnetic field H encircling it, AND a time-changing electric flux D generates a magnetic field H encircling it |




| Band | Frequencies (GHz) | Wavelengths (mm) | Comments |
| P band | 0.23-1 | 1303.4-299.8 | |
| L band | 1-2 | 299.8-149.9 | Long wavelength can pass through most structures, but heavily allocated; GPS is at 1227.6 (L2) and 1575.42 (L1) MHz |
| S band | 2-4 | 149.9-74.95 | Mobile phones, wireless Ethernet; microwave ovens use 2.45 GHz |
| C band | 4-8 | 74.95-37.47 | Wireless Ethernet around 5 GHz; satcom downlinks 3.4-4.8 GHz, uplinks ~6 GHz |
| X band | 8-12 | 37.47-24.98 | Used for military satellites |
| Ku band | 12-18 | 24.98-16.66 | Nearly as good penetration as L-band, with a higher data rate, but likewise mostly allocated; downlinks use 10.7-12.75 GHz range |
| K band | 18-27 | 16.66-11.10 | Affected by a water-vapor absorption line peaking at 22 GHz; some sources consider “K band” the entire 12-40 GHz region |
| Ka band | 27-40 | 11.10-7.495 | Lots of open spectrum, but needs high TX power and is subject to rain fade; potential for mobile comms with beam-steering antennas |
| V band | 40-75 | 7.495-3.997 | Very strong oxygen absorption band peak at 60 GHz |
| W band | 75-110 | 3.997-2.725 | Between peaks in oxygen absorption band |
| mm band | 110-300 | 2.725-0.9993 | Millimeter waves; secondary O2 absorption peak at 120 GHz |
| µ mm band | 300-3000 | 0.9993-0.09993 | Emerging uses for imaging (T-rays) |
| Band | Range (GHz) | Wavelengths (mm) | Comments |
| Q band | 40-60 | 7.495-4.997 | Sometimes “U band” |
| E band | 60-90 | 4.997-3.331 | |
| F band | 90-140 | 3.331-2.141 | |
| G band | 140-220 | 2.141-1.363 |


| 9 | message error |
| 10 | instrumentation (distinguishes status word from command word) |
| 11 | service request (RT indicating it has data to send) |
| 12-14 | reserved (always 0) |
| 15 | broadcast command received |
| 16 | busy (RT unable to transfer data to/from a subsystem) |
| 17 | subsystem flag (fault in a subsystem) |
| 18 | dynamic bus control acceptance (RT acknowledging command to take over as BC) |
| 19 | terminal flag (fault in RT hardware) |



| Letter | Morse Code | US WWII Phonetic | NATO Phonetic |
| A | ·- | Able | Alfa |
| B | -··· | Baker | Bravo |
| C | -·-· | Charlie | Charlie |
| D | -·· | Dog | Delta |
| E | · | Easy | Echo |
| F | ··-· | Fox | Foxtrot |
| G | --· | George | Golf |
| H | ···· | How | Hotel |
| I | ·· | Item | India |
| J | ·--- | Jig | Juliett |
| K | -·- | King | Kilo |
| L | ·-·· | Love | Lima |
| M | -- | Mike | Mike |
| N | -· | Nan | November |
| O | --- | Oboe | Oscar |
| P | ·--· | Peter | Papa |
| Q | --·- | Queen | Quebec |
| R | ·-· | Roger | Romeo |
| S | ··· | Sugar | Sierra |
| T | - | Tare | Tango |
| U | ··- | Uncle | Uniform |
| V | ···- | Victor | Victor |
| W | ·-- | William | Whiskey |
| X | -··- | X-ray | X-ray |
| Y | -·-- | Yoke | Yankee |
| Z | --·· | Zebra | Zulu |
| 1 | ·---- | One | Wun |
| 2 | ··--- | Two | Too |
| 3 | ···-- | Three | Tree |
| 4 | ····- | Four | Fower |
| 5 | ····· | Five | Fife |
| 6 | -···· | Six | Six |
| 7 | --··· | Seven | Seven |
| 8 | ---·· | Eight | Ait |
| 9 | ----· | Nine | Niner |
| 0 | ----- | Zero | Zero |